With the proliferation of mobile apps, their security becomes critical: apps store and transmit a lot of sensitive user data. This data can be vulnerable due to weak encryption, insecure storage, and insufficient API protection.
Traditional data protection methods are no longer sufficient for today's mobile environment. Today, developers need to consider not only local but also network threats, such as Man-in-the-Middle attacks and weak SSL connections. Vasilii Domnikov, co-founder of the IT company Magora, analyzes modern methods of protecting user data in mobile applications, examines the most common threats, and offers practical solutions that can help developers prevent leaks and vulnerabilities in their products.
Mobile apps have become an integral part of our digital lives, yet they pose significant risks to user data. Given that apps can transmit, store, and process vast amounts of data, developers must take steps to ensure their security. In reality, many apps remain vulnerable due to weak encryption, API manipulation, and insecure data storage.
Ensuring data security in mobile apps is critical for businesses. First, data breaches undermine user trust and can lead to mass app deletion. Studies show that 65% of users lose trust after such incidents. Second, it threatens serious financial losses: fines, lawsuits, and reduced revenue. In 2023, the average cost of a data breach was $4.24 million dollars. Finally, legal requirements such as GDPR and CCPA oblige companies to protect data, and violating them can lead to large fines and legal consequences.
With ever-increasing cyber threats, traditional methods of protecting data on mobile platforms are becoming insufficient. According to a Symantec study, in 2023, about 60% of mobile apps will contain at least one serious vulnerability that could lead to a data breach. Every year, the number and sophistication of attacks on mobile apps increase, and attackers are finding more and more sophisticated ways to bypass existing security measures.
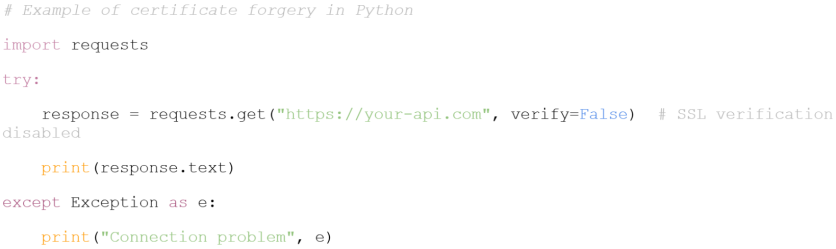
Today's mobile data security threats are many and varied. The most common issues include data leaks, API manipulation, and insecure data storage. For example, user data can leak due to poor security, and unsecured APIs are vulnerable to attacks such as Man-in-the-Middle (MITM). If an application does not authenticate the SSL certificate, attackers can intercept data transmitted between the application and the server.
There are various tools and frameworks for analyzing data security. One of them is the OWASP Mobile Security Testing Guide (MSTG). The MSTG is a guide that provides standards and practices for secure development, threat examples, and step-by-step instructions for testing mobile applications. It helps developers gain a better understanding of security and avoid common mistakes. Snyk and Veracode are two other important tools that help find and fix vulnerabilities during the development phase by integrating them into CI/CD. They can be used to automate code scanning and prevent threats before application release.
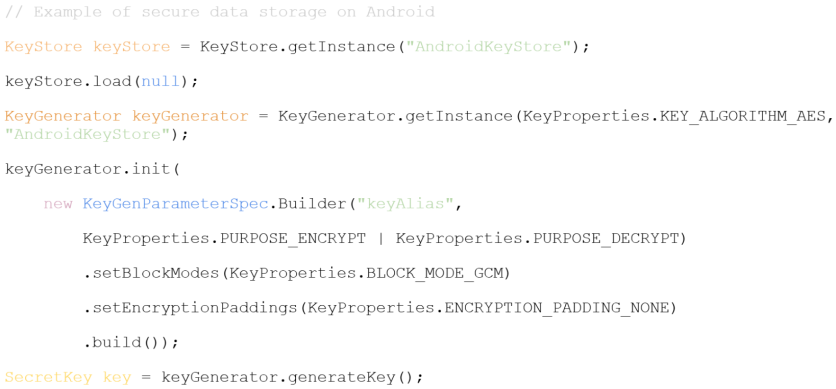
Practical code examples and solutions allow developers to implement security practices and avoid bugs. For example, securely storing data on the device is one of the important aspects of mobile app security. In Android, you can securely store data using KeyStore API keys. Using KeyStore API ensures that data is protected even if the device is physically accessed.
Another important example is analyzing the security of API requests with Burp Suite. This tool allows developers to analyze application requests to the server and check data encryption. If an application uses an insecure connection, Burp Suite can capture and analyze such vulnerable requests, preventing possible MITM attacks.
The advantage of Burp Suite is that all its utilities and additional plug-ins can easily interact with each other. In the browser settings, you can specify Burp Suite as a proxy server (for HTTPS sites, you will need to install the TLS certificate Burp created). This will allow all browser activity, including requests sent and responses received, to be stored in the Burp Proxy. In addition, you can redirect HTTP traffic to Burp from mobile applications and other desktop or IoT devices. Requests stored in Proxy can be sent to other modules for more detailed analysis and operation.
Mobile application security analysis should be built into the development and CI/CD process so that vulnerabilities can be identified early and addressed before release. By following OWASP guidelines, using automated code analyzers, and applying encryption at the storage layer, developers can effectively protect user data even if the device is physically accessed.
Thus, implementation of OWASP MSTG, code analyzers, and tools such as Burp Suite can minimize risks and ensure reliable protection of user data.
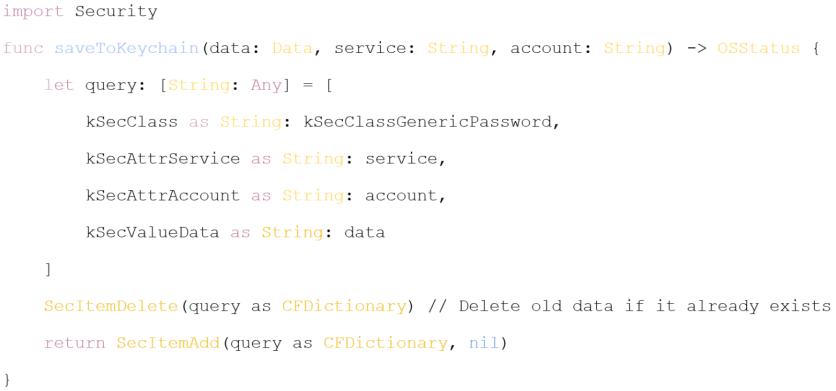
To ensure data security at the development stage, it is important to take into account the specifics of each mobile platform. For example, iOS and Android have different encryption mechanisms and security policies. In iOS, data can be stored securely using Keychain Services, which allows you to encrypt data tied to a specific device. An example of code to securely store data in Keychain might look like this:
In addition to analysis tools such as Snyk and Veracode that find vulnerabilities in code, developers can use tools to analyze third-party libraries that often turn out to be the source of threats.
Mobile Security Framework (MobSF) is another powerful tool that can analyze Android APK files and iOS IPA files to identify vulnerabilities in the application and in the dependencies used. MobSF can be integrated into CI/CD processes to warn of risks before the application is deployed.
In addition, penetration testing helps to understand how secure an application is under real-world threats. By simulating attack scenarios such as SQL injection, XSS, or brute force attacks, developers can address weaknesses before the application is available to users.
Following DevSecOps principles is another important aspect of protection. Implementing DevSecOps allows security processes to be integrated into every phase of development and testing, making the entire team more accountable for data protection. For example, tools such as Aqua Security or Checkmarx can be used to scan automatically during the code writing and integration phase. This allows you to not only identify vulnerabilities but also offer real-time solutions to developers, minimizing risk.
For a comprehensive approach to data protection in mobile applications, it is important to combine secure storage practices, regular testing, and automation of vulnerability analysis. This allows developers to keep user data securely protected, reducing the risks of leaks and unauthorized access even in the face of ever-changing threats.





