The digital threat landscape continues to evolve as cyberattacks rise annually, seemingly without end. A report from the Fortinet Ransomware Survey published in 2021 shows a 1,100% increase in ransomware attacks. Thus, staying on top of attack trends has become ever-more critical in our vulnerable day and age. Organizations must adopt a zero-trust model to implement security across all layers of the digital estate so as to eliminate any potential threats before costing the business's financial health.
Why implement Zero Trust?
The Zero Trust model features principles that verify every transaction, assert the least privilege access, and assume breach to minimize the impact of threats when detected. Implementing its solutions improves a company's security posture through automated controls and increased visibility. Only authorized users can access corporate resources based on policy guidelines. Each device, network, and application is continuously monitored to prevent the likelihood of breaches and other security incidents.
Outlined below are the top 5 best Zero Trust solutions in 2023:
1 SSH Zero Trust Suite

Overview
SSH Zero Trust Suite combines the proven-in-use secure communications software modules into a modern, easy-to-use solution. The suite enables customers to securely communicate between people, applications, networks, and systems without artificial walls, like firewalls, VPNs, or demilitarized zones (DMZ). The solution enables passwordless, keyless, and borderless security, equalizing cybersecurity threats across the internet, extranet, and intranet environments. It preserves data confidentiality and audibility, allowing proper access controls and monitoring.
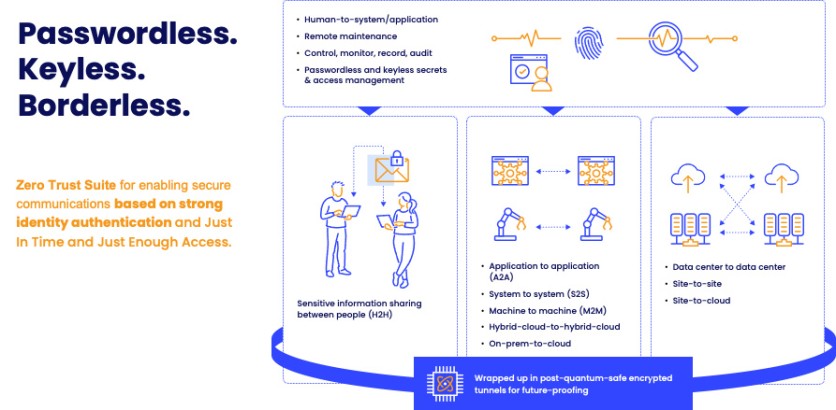
SSH Communications Security (SSH) is a cybersecurity company specializing in securing communications between people, applications, networks, and systems, including privileged access and credentials management.
This helps companies build a proactive defensive cybersecurity posture to reduce the risk of breaches and lets organizations grow in the digital world without constant worry about attacks and leaks.
SSH is trusted by over 5,000 customers worldwide, including Fortune 500 companies, government agencies, financial institutions, retailers, and top manufacturers.
SSH discovers credentials and privileged power user accounts while detecting vulnerabilities and weaknesses in advance to mitigate the risk of breaches and other security incidents. The company protects mission-critical digital assets to secure businesses in the age of the hybrid cloud, which has pushed organizations to adapt to the complexity of modern IT as well as OT environments with a Zero Trust model.
The Zero Trust solutions of SSH work in all environments, ranging from traditional on-premises technologies to modern cloud-based tech, like container architectures and Kubernetes orchestrated environments. Sensitive information remains secure and accessible only to authorized users or machine IDs, thanks to robust encryption and strong identity-based authentication. It also monitors and audits sessions and activities, regardless of whether data is in transit, at rest, or in use.
While it also supports traditional credential vaulting and rotation, SSH's Zero Trust Suite eliminates passwords and incorporates biometric and other passwordless or keyless authentication methods to ensure a smooth user experience and enhanced security. It provides just-in-time authentication between people, applications, systems, networks, and clouds.
Features
Zero Trust Suite features three software modules whose solutions safeguard the most critical assets and offer a secure workspace where authorized users can collaborate.
PrivX - Hybrid Privileged Access Management
PrivX mitigates insider and third-party risks by enabling passwordless and keyless authentication. It enhances privileged access security by adopting zero-trust authentication methods, such as single sign-on and multi-factor authentication.
The access management module restricts access by permission or role, only allowing users to see and select targets available to them. Authentication is done automatically with integration via an identity management system, and access is granted just-in-time, without anyone seeing or handling access secrets. The just-in-time authorization token contains all the secrets needed for the session and expires automatically after the session, leaving no secrets to be managed.
If short-lived tokens cannot be used, this Zero Trust solution utilizes other authentication methods, such as public keys or traditional passwords. PrivX vaults and rotates the secrets, ensuring no leakage against threats.
Universal SSH Key Manager
Universal SSH Key Manager (UKM) reduces the stress of key management complexity by automating the governing of keys based on compliance and security standards. It discovers at-risk keys to demonstrate the scale of the potential associated risk, averting holes in the businesses' defenses. Typically, organizations have ten times more authentication keys than passwords but no means to manage all those keys at the necessary scale.
After the discovery phase, UKM allows organizations to replace weak or old keys with more secure algorithms without the risk of operational disruptions. It's worth noting that the solution is particularly adept at managing keys required for application-to-application or machine-to-machine, which often make up to 80% of all connections in a large enterprise.
When the key estate is under control, UKM provides mechanisms to migrate SSH access to keyless, just-in-time Zero Trust access with short-lived tokens. This radically reduces key management overhead and improves security. The module uses its knowledge from its risk assessment of the entire server estate to move the access away from the keys into PrivX, where secrets are stored within short-lived tokens to prevent anyone from seeing or handling them.
Internal and external auditors receive reports with the latest evaluation and executive summary on the level of compliance with regulations and standards such as NIST, PCI-DSS, and more.
Secure Collaboration and Communications
The secure Collaboration and Communications module centralizes all human-to-human and automated data sharing into a single solution. It conducts verifications of the sender and recipient whenever sensitive information is being collected, shared, transmitted, signed, used in instant messaging, or collaborated on. Adopting the principle of the Zero Trust model, authorized users can share sensitive files among internal stakeholders and third parties without the risk of data disclosure due to strict controls and policies enforced whenever sensitive data is in transit or being accessed.
The module allows users to isolate sensitive information from public clouds or Microsoft or Google ecosystems or embed the solution as an add-on to them. It enables organizations to receive sensitive information in a simple fashion, e.g., from their own web page, without the sender having to install anything. The solution has been certified by a national authority for secret-level communication.
It also applies various authentication methods, from passports to bank IDs, to prevent threat actors from gaining access. It logs all user activities for full audit trails. Users can enjoy high availability and security for file sharing with its multi-protocol support and role-based access control.
The solution allows building batch file sharing, file transfer, or automated connections between applications, networks, servers, or systems without having to change scripts. Full authentication for file and patch transfers ensures file integrity and safety in any environment.
The solution protects long-term secrets against future threats with quantum-safe cryptography, which ensures that transmissions are secure over open public networks.
SSH offers 24/7 enterprise support for its Zero Trust solutions. From secure data management to passwordless and keyless authentications, extending to secure file transmissions and storage, SSH Zero Trust Suite is a modern and secure solution that any organization can use against the risk of credential misuse, management complexity, and rising costs.
2 Absolute ZTNA

Overview
Absolute ZTNA offers a software-defined perimeter through Zero Trust Network Access. It creates a context-based boundary around a set of applications, making them invisible to unauthorized users wherever they are hosted. It performs threat detection and prevention, ensuring uninterrupted secure access. It maintains the same user experience, even for remote workers, driving productivity while maintaining the security of a company's critical resources.
Features
Absolute ZTNA enforces consistent policies for all user access, applying Zero Trust Network Access principles for secure and optimized remote access. Admins can control access to the Web and cloud applications based on risk and other contextual factors such as geolocation, network connection, and user device security posture.
It also offers malware protection by rendering websites in isolated containers located on remote servers far from the endpoints where threats can't reach them. With dynamic ZTNA policies, Absolute ZTNA eliminates chokepoints and protects device data. These policies strengthen the Zero Trust security posture, heightening employee protection and restricting lateral movement against cyberattacks so you can rest easy knowing your business is digitally secure.
Absolute ZTNA also features a resilient, self-healing infrastructure for cloud and on-premises deployment. Hence, it can automatically repair itself if it's tampered with, accidentally removed, or malfunctions. An optional secure web gateway service provides a seamless browsing experience for hybrid or remote workers while keeping threat actors at bay to prevent data loss or leakage. It is a secure remote access solution with broad OS support.
3 GoodAccess

Overview
GoodAccess is a cloud-based Zero Trust network access solution designed for small and medium businesses. It offers bulletproof defense against breaches with access management rules, traffic encryption, multi-factor authentication, SSO, and other features. It also provides high-speed connectivity, enabling a smooth user experience even for team members who work remotely.
Features
GoodAccess simplifies identity management and access control with a single sign-on solution. It supports SCIM integration for automated access provisioning, besides aligning with access credentials from Microsoft Azure, Google Workspace, Okta, and other SAML-compatible services.
It features a Threat Blocker that prevents users from accessing compromised or dangerous websites that can fall victim to malware, phishing, command and control botnets, and other ploys of threat actors. It guarantees constant protection through threat intelligence feeds and DNS blacklists.
GoodAcess also logs every user activity so admins can more easily and completely control gateway access points, reducing risks and increasing compliance with GDPR, SOC2, or HIPAA regulations. With virtual access cards, admins can determine the level of access an authorized user has to a specific system.
The Zero Trust network access solution also contains built-in cloud and branch connectors so users can access their clouds, data centers, and private LANs from a single virtual infrastructure. Users can also set up a redundant IPsec or IKEv2 tunnel as a failsafe, concealing end-users and resources from threat actors for multi-layered security.
4 Citrix ZTNA

Overview
Citrix Secure Private Access is a modern cloud-delivered Zero Trust Network Access solution that prevents unauthorized access and eliminates threats, driving productivity for hybrid and remote workforces without exposing networks to threat actors. It continuously evaluates risk factors throughout each session. When it detects suspicious activity, it automatically enforces security controls, changing users' authority when interacting with corporate apps.
Features
Citrix ZTNA offers single sign-on to all web and SaaS apps, consolidating multiple access points to create a seamless user experience. It features adaptive authentication and adaptive access control policies to monitor suspicious user activity, continually scanning the device throughout each user and app session to prevent insider threats and other security risks.
Admins can also set security controls based on user risk scores, locations, and device postures. They get to determine who is granted access based on job roles, locations, devices, and more due to the adaptive authentication of Citrix ZTNA. The solution also offers the option to screen record the activity of any user session to monitor based on industry requirements.
With a personalized risk score, Citrix ZTNA offers a picture of all network traffic, users, files, and endpoints, making it easier for organizations to stay ahead of internal and external threats before they evolve into potential breaches. It scans the user's device both before and after a session is established, ensuring well-rounded security and protection of the company's many various assets.
5 JumpCloud

Overview
JumpCloud is a Zero Trust Security solution that secures access to critical resources, enforces dynamic access policies, and verifies identities and devices frequently. It acts as an open directory platform that unifies the technology stack across identity, access, and device management cost-effectively with its robust features and easy-to-use interface. It also contains a catalog of pre-built and open integrations to reduce the number of point solutions needed to keep operations running smoothly.
Features
JumpCloud's conditional access policies control resource access based on dynamic and situation properties. Admins, for example, can require additional authentication factors at login or prevent entry for users operating from an open, unsecure network.
With multi-factor authentication, the platform prevents unauthorized logins and fosters a seamless end-user experience. Admins can choose between flexible authentication, contextual access, or easy enrollment to secure user access.
JumpCloud also features a password manager where users can create, store, and protect credentials locally on their devices and manage their passwords. Every privilege, password, and security is displayed in a single console, making blocking access from malicious actors easier.
It also simplifies directory data monitoring and management. JumpCloud features Directory Insights, providing a complete real-time picture of every user's identity, device, and resource. It aggregates and standardizes event logs and generates actionable data for quick resolutions. With a clear audit trail, organizations can more easily meet industry standards and procedures to receive certifications from SOC 2, HIPAA, and more.
Conclusion
Traditional security models leave gaps for unchecked threat actors to roam freely within a corporate network, raising a cyberattack's potential scale and severity. Zero Trust offers a strict approach to cybersecurity, assuming a network has already been compromised to minimize risks caused by trusting even authorized users. Choose among the top five best zero trust solutions to ensure protection from all threats and improve the company's security posture.




