A new phishing campaign has been spotted by cybersecurity leader Armorblox, stealing user credentials by mimicking a message notification from a company with email encryption.
Phishing attacks remain one of the most common strategies used by cybercriminals to steal user credentials from unsuspecting users. It usually aims to snag the username and password and uses it to steal more or access and control an entire organization's network. Unfortunately, phishing attempts are becoming more and more believable in their impersonation of legitimate business emails.
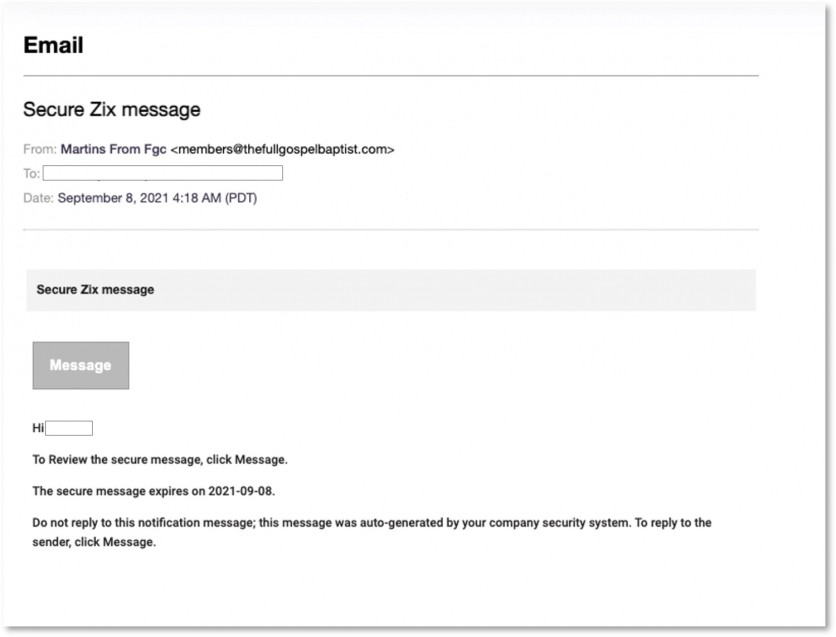
Armorblox Report on Zix Phishing
In its independent report, Armorblox details a credential phishing attack that spoofs and encrypted message notifications from Zix. This affected Google Workspace, Microsoft Exchange, and Microsoft 365, with the emails ending up in some 75,000 mailboxes. The campaign used the title "Secure Zix message," and claimed to be a secure message from Zix. When a user clicks a link, the attachment downloads an HTML file onto the target system.
When the phishing email was compared with an actual template for Zix secure messages, there were differences, yet the fake was enough to trick unsuspecting victims. The domain used in the cyberattack was "thefullgospoelbaptist.com," the name of a religious organization established in 1994. While the URL no longer works, Armorblox believes that the attackers might have exploited an older version of the domain to send the phishing emails. The email was able to pass standard authentication checks such as SPF, DMARC, and DKIM.
While security measures still managed to capture and block the final HTML file, the attackers had ingenious methods to let their emails pass security. By spoofing email encryption services like Zix, the phishing email appears to have a layer of its security. Adding this to a supposed "expiration date," the email creates a sense of importance and urgency.
It managed to bypass certain security measures since the email is similar to an actual Zix template. Also, the parent domain was a legitimate link, helping the phishing emails pass authentication processes.
How to Protect Yourself and Your Organization
Armorblox makes these three suggestions to boost your and your organization's defenses in the middle of this ongoing phishing campaign:
- Improve your local email security with additional controls. The Zix phishing emails reported by Armorblox got through the standard defenses of Microsoft 365, Google Workspace, Cisco ESA, and Microsoft Exchange. For better defenses, improve your existing email security with additional layers that use different protocols. Gartner has published a Market Guide for Email Security that highlights the latest approaches from various developers.
- Keep an eye on social engineering clues. While this requires a trained eye to immediately identify red flags for phishing emails, it always starts with careful observation of incoming emails, especially for the small details. Look out for elements like the sender's name and email and anything different about the language used in the message.
- Follow best practices for security and password. Your account credentials are your responsibility, and this includes not using common passwords and those based on your personal information like birthdays. This also includes not using the same password for multiple accounts. For people finding difficulty maintaining multiple passwords, password managers can help you with the task.
RELATED ARTICLE : Microsoft Discovers New Morse Code Phishing Attack: Cybersecurity Experts Confirm It is Effective
Published on Tech Times.




