Microsoft's latest discovery about phishing reveals an unusual as-a-service operation that makes use of phishing kits for cloud services.
The tech giant's cybersecurity team said that there are different services that the hackers use, including email delivery and fake login pages.
Microsoft Uncovers As-a-Service Phishing Operation
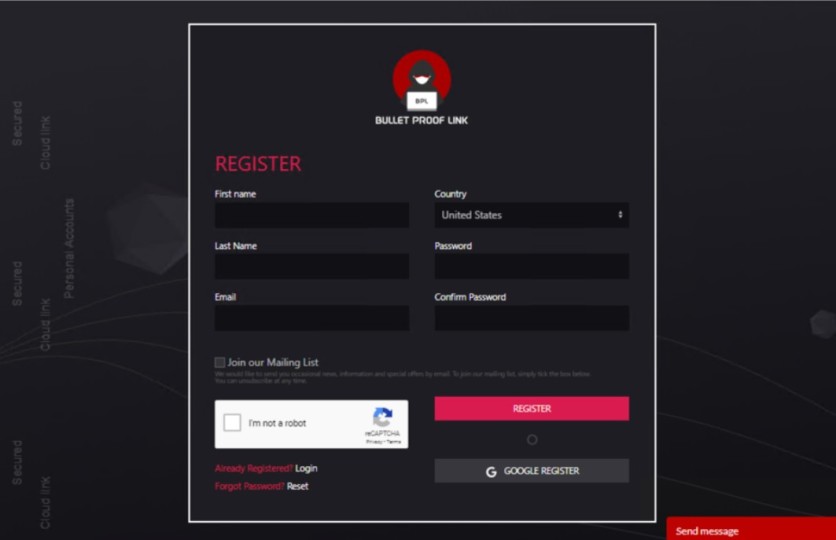
According to a blog post by the Microsoft 365 Defender Threat Intelligence Team, the attackers depend on the malicious pages and links that are sent to the victims.
The cybercriminals will inject malicious software into the system to steal important credentials from the user.
What's unique about this phishing attack is the fact that the untested stolen credentials are directed to the hackers. This means that despite not gaining access to the system, the hackers could still carry out the operations.
Many businesses nowadays have an established domain for their pages. Most importantly, they have created login pages for the ease of user's access to the website.
The phishing-as-a-service operation has reportedly hit the cloud services, such as OneDrive, Google Docs, American Express, LinkedIn, and more.
The dangerous part of this attack could result in double theft where the attacker could offer the credentials using the original account of the provider. Later, another recipient could buy the stolen credentials that will be sold by the hacker.
BulletProofLink Service Linked to 300,000 Compromised Subdomains
From ZDnet's updated report published on Wednesday, Sept.22, the Redmond company aims to tighten the security protection for the companies.
The case of a phishing-as-a-service does not involve ZIP-filed phishing kits. Instead, the templates to create fake selling login sites are contained in the whole package.
During the investigation, Microsoft said that a surprising number of 300,000 subdomains were hit by the attack.
The tech titan even called it an "infinite subdomain abuse."
"These subdomains" allow attackers to use a unique URL for each recipient while only having to purchase or compromise one domain for weeks on end," Microsoft said.
Read Also: Latest Email Scam Targets Gmail, Outlook Users: How to Avoid this Vishing Attack?
Microsoft Issues Warning on Phishing Links
Last August, Microsoft cybersecurity researchers concluded that some attackers use a traditional phishing method to exploit their victims.
Using the Morse Code, there is a chance that the hackers could bypass the system's security. Despite the availability of new techniques, the Morse Code is still considered an effective tool for phishing.
The tech service provider said that the company logo of the target could be seen along with the package of malicious credentials bearing a bogus Microsoft 365 login.
Later that month, there was another attack that exposed 3,300 firms. The vulnerability uses casual URLs that look like a reliable domain in the first place.
Once the details are encoded, a fake sign-in page will appear. It will also use Captcha verification to deceive the victim. The phishing tactic will start when the user clicks the link.
Read also: Recent Phone Scam Annoys Victims Through Spamming Phone Calls: Beware of This Seven-Digit Number
This article is owned by Tech Times
Written by Joseph Henry




