With the recent news that hackers can now jailbreak T2 chips in Macs and MacBook as well as the various malware that targeting these devices, Apple's security is being challenged.
Thomas Reed, director of Mac & Mobile at Malwarebytes said during the JNUC event last week that around 84% of Mac malware are simply Potentially Unwanted Programs and adware while only 0.3% of these malware that targeted Mac is truly threatening. "It's not a large slice of the pie, but it's still something to be wary of," Reed said.

Most of these malware attacks are presented as BirdMiner, ThiefQuest, or Lazarus. BirdMiner is a cryptominer that was spread via audio apps pirate versions and installs a virtual machine called Qemu. ThiefQuest is a ransomware that can be downloaded via torrent file-sharing sites through modified copies of legitimate apps, which also install malware.
Meanwhile, the North Korea's Lazarus group actively develops Mac malware, including DaclsRAT, Fallchil, and GMERA, which create backdoors into affected systems. These are mainly distributed as legitimate apps.
Jailbreaking T2 chips
The T2 security chip is a special co-processor a separate CPU that is installed on MacBooks laptops as well as modern Apple desktops such as Mac mini, iMac, and Mac Pro, alongside the main Intel CPU. These chips handle audio processing, different low-level I/O functions as well as handle most security features in all Apple devices sold since 2018.
Hackers have revealed in Twitter and Reddit that combining two exploits called Checkm8 and Blackbird, which were used for jailbreaking iOS devices break T2 chips and run code inside these chips during its boot-up routine to alter its normal behavior. This technique will allow users to control their devices fully, including altering behavior of core OS, retrieving encrypted data, or even planting malware.
According ironPeak, a Belgian Security firm, the technique works because Apple has kept open a debugging interface in the T2 security chip, "allowing anyone to enter Device Firmware Update (DFU) mode without authentication."
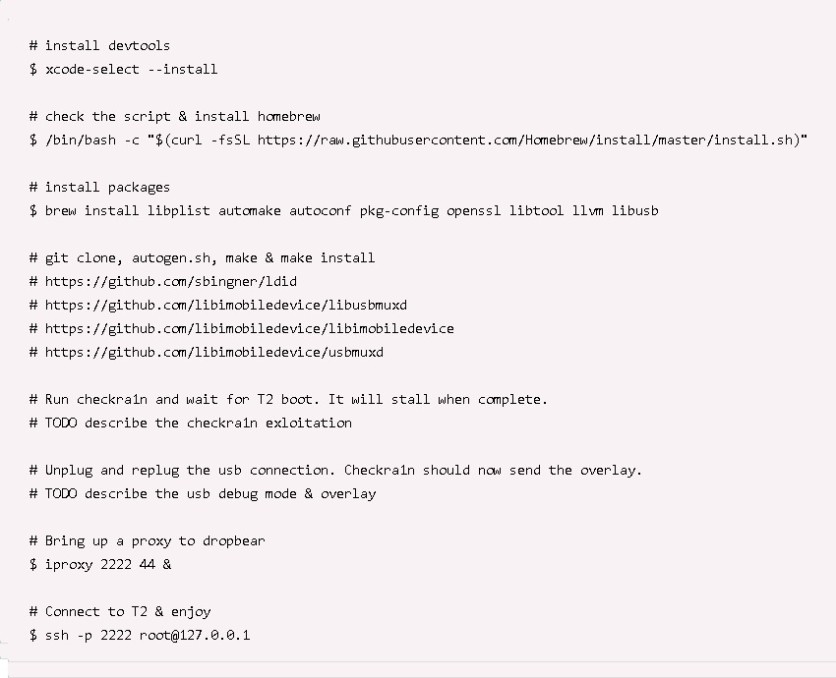
This new jailbreaking technique is highly dangerous to any Mac or MacBook that was left unattended as evil maid attack can be easily employed by connecting a USB-C cable, then reboot the device, and run Checkra1n 0.11.0.
While this method can be used for new law enforcement investigation tools to allow detectives to access a suspect's Mac or MacBook to retrieve encrypted vital information, this would still pose a great risk to users, particularly those who are travelling as they submit their computers before they could cross borders. Worse, businesses that employ large fleets of Macs and MacBooks are exposing all these products to attacks.
How to protect Mac and Macbook devices from attacks
With the frequency of attacks on Mac and Macbook makes these devices no longer are invincible as how Apple presented them at first. Thus, users must act to ensure the safety and security of their devices.

While Apple continues to work on improving its security in all its devices, here are some actions apple owners can do to prevent any attacks:
- Avoid leaving the Mac and Macbook unattended. Since the T2 chip can be easily hacked using evil maid attack, keeping the computers locked when not in use would be the easiest way to protect it.
- Avoid clicking on an unfamiliar link sent via email. It has been known already that most malware are spread through emails, so users should be extra careful with spam emails they receive.
- Avoid opening attachments like Word documents or other files from unknown senders. This will put the device at high risk for attacks.
- Avoid installing software from any source aside from the approved App Store to avoid harming the devices, particularly when it is used for work.
Extreme caution should be employed at all times to prevent any attacks.
Read also : Warning! Hackers Bypass Apple's T2 Security Chip By Combining Two Exploits Used to Jailbreak iPhones
This is owned by Tech Times
Written by CJ Robles

![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)


