Securing remote work environments has become a concern for businesses as the demand for flexibility and improved work-life balance drives its adoption. Most of the time, remote teams require access to the same internal services, applications, and information as they would in the office. Organizations must upscale their cyber risk management strategies to address the unique threats employees face working remotely.
Remote work offers several benefits, transforming business operations by providing flexibility, boosting productivity, and expanding access to a broader talent pool. However, it also presents challenges regarding cybersecurity. Organizations must take the necessary precautions to safeguard their IT assets, ensuring the costs of a cyber breach do not overshadow the advantages of employees working offsite.
Cybersecurity Challenges of Remote Work
Here are some cybersecurity challenges associated with it.
- Endpoint security: Employee endpoints may lack necessary security updates, antivirus software, or adherence to security policies, exposing organizations to significant risks. Organizations must implement effective endpoint security measures to mitigate these risks and protect data. This may involve the implementation of an Extended Detection and Response (XDR) solution, Multi-Factor Authentication (MFA), regular patch updates, and continuous security monitoring.
- Expanded attack surface: Remote work expands an organization's attack surface as employees connect from various locations using multiple devices and networks. This creates more entry points for cybercriminals to exploit. Organizations can improve their security posture by utilizing advanced threat detection tools such as Security Information and Event Management (SIEM) to address this risk. This helps organizations to monitor and identify suspicious activities and anomalies on remote endpoints.
- Access control: Working offsite increases the risk of credential theft and insider threat, which could lead to a cyber breach. Organizations should implement access control measures like MFA and role-based access control (RBAC) to ensure remote employees access only necessary resources. Additionally, monitoring access and changes to sensitive files and systems using a file integrity monitoring tool should be a priority.
- Insecure networks: Remote employees often use home Wi-Fi or public networks, which lack corporate security controls, making them more vulnerable to cyberattacks like man-in-the-middle attacks. Without proper network security protocols, offsite work may expose employee devices and company data to these threats. To mitigate these risks, organizations can enforce virtual private networks (VPNs) for encrypted communications, allowing employees to access the company's resources securely.
Safeguarding Remote Work with Wazuh
Wazuh is an open-source Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) platform. It provides capabilities for safeguarding remote work environments. These capabilities include endpoint monitoring, access control, compliance, and incident response, among others, to address the diverse security needs of different organizations. The following section shows how Wazuh helps secure a remote workforce environment.
Endpoint Security
Wazuh addresses endpoint security for remote workforces by leveraging its XDR capabilities. Wazuh XDR offers log analysis for malware detection, vulnerability detection, configuration assessment, and compliance monitoring, providing coverage for remote endpoints. Wazuh monitors endpoints for suspicious activity, quickly alerting security teams to potential risks. Its incident response capability enables organizations to automate threat mitigation on remote endpoints, such as blocking malicious IPs or stopping unauthorized processes, enhancing endpoint security.
Organizations can actively respond to and contain threats like malware or ransomware before they impact the organization by leveraging Wazuh Active Response capability. For example, organizations can use Wazuh to detect Daolpu infostealer. Daolpu infostealer is delivered through phishing emails that contain a Microsoft Word document attachment with malicious macros. This malware collects login credentials, browser history, and cookies in Google Chrome, Microsoft Edge, Firefox, and other web browsers.
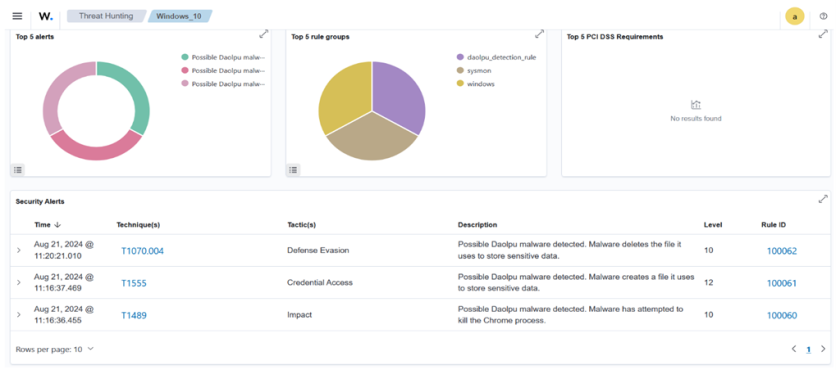
Detecting Unauthorized File Access
The Wazuh File Integrity Monitoring (FIM) capability helps address access control challenges in offsite work environments by continuously tracking and logging changes to critical files and directories. With FIM, Wazuh detects unauthorized or suspicious modifications to sensitive files, which could indicate unauthorized access attempts or credential misuse. These changes are immediately logged and can trigger alerts, enabling swift response to potential security incidents.
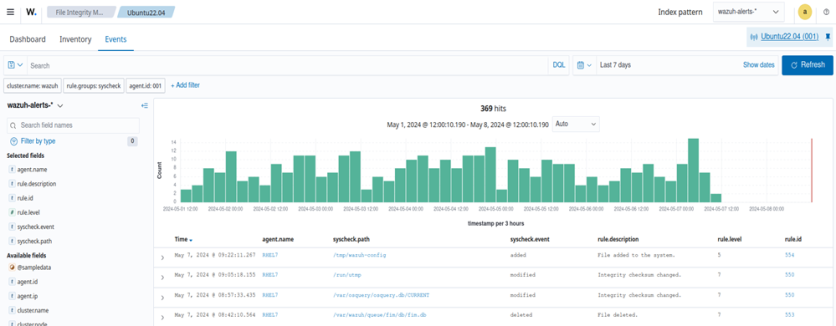
An alert is generated whenever the monitored file or directory is modified, as shown in the image above.
Virtual Private Networks (VPNs) and Firewall Log Monitoring
Wazuh enhances network security for remote work by collecting and analyzing logs from VPNs and firewalls to provide detailed insights into network traffic connections. Wazuh leverages its XDR capabilities and GeoIP to enhance VPN and firewall monitoring. Organizations can leverage Wazuh to analyze logs from VPN servers and firewalls, enhancing the security of their distributed workforce and ensuring protected access to sensitive data. For example, organizations can configure Wazuh to monitor their OpenVPN users by using its GeoIP feature.
SCA and Regulatory Compliance
Wazuh addresses inconsistent security policies by enforcing standardized configurations through its Security Configuration Assessment (SCA) capability, which continuously checks endpoints for compliance with organizational security policies. Wazuh SCA supports custom policy templates tailored to specific standards, enabling organizations to enforce critical security practices such as timely updates and strong password policies. The SCA capability also assesses endpoint configurations against standardized policies, like CIS benchmarks, detecting non-compliance on remote devices. For instance, organizations can create the custom SCA policy below to check the Windows password policy across remote workstations using Wazuh.
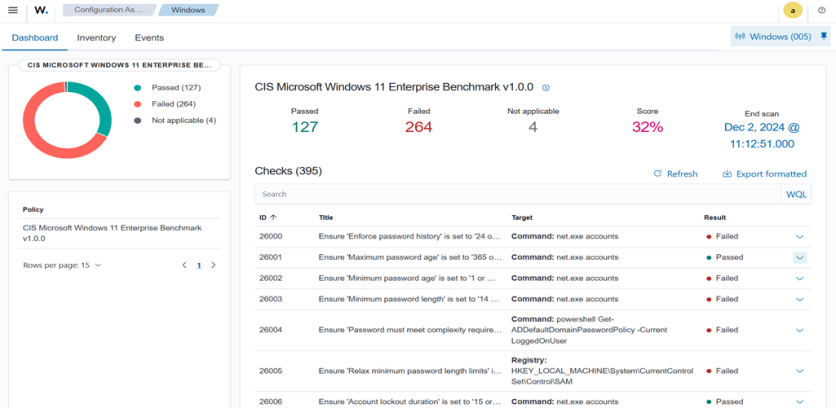
Additionally, Wazuh regulatory compliance capabilities help organizations meet industry-specific standards by regularly assessing endpoint configurations against PCI DSS and GDPR benchmarks. This helps in promoting a consistent and compliant security posture across remote devices.
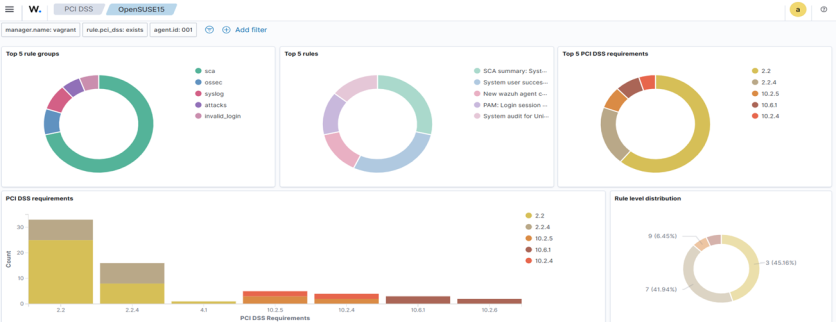
Conclusion
Wazuh provides a comprehensive platform for securing remote work environments by enabling the monitoring of endpoints, network traffic, file integrity, and access control. Organizations can utilize Wazuh capabilities to ensure that their remote workforce operates securely, with proactive detection and response.
Learn about Wazuh by exploring their documentation and joining their user community.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




