
Many organizations lack the tools to protect and secure data, as records show over 3200 instances of data compromise happened in the US last year, according to ITRC's data breach report. Data loss harms businesses of all sizes as threat actors have found new ways to access networks. Data loss prevention (DLP) software can detect and prevent the loss, leakage, or misuse of data by monitoring and analyzing data to identify potential violations of security policies.
Data loss prevention tools safeguard data from accidental or intentional exposure, saving businesses from the risks of data breaches and unauthorized access. Data threats can manifest as cyberattacks, malware, insider risks, phishing, or unintentional exposure. Companies can leverage the best DLP software to monitor sensitive data, who has access to it, and how it is used. The tools can help them respond to potential breaches or data loss prevention policy violations.
Discover five of the best DLP software for preventing inadvertent leaks or intentional breaches and strengthening the cybersecurity posture.
#1 Zecurion Next Generation DLP

Overview
Zecurion offers easy-to-manage and easy-to-implement Data Loss Prevention (DLP) solutions with enterprise-level protection. Its Next Generation DLP employs a people-centric approach designed to safeguard companies from insider threats. This software provides a comprehensive view of all processes by monitoring all events, files, and documents, and offers user behavior analytics for proactive threat detection.
Zecurion provides a wide range of DLP deployment options and its solutions can be enhanced with Secure Web Gateway, and Data-Centric Audit and Protection. It boasts 10+ data classification techniques, including digital fingerprints for documents, images, source rows of target databases, morphology tools, and more.
Zecurion offers audit and control over critical data through its Data-Centric Audit and Protection (DCAP), an agent-based solution. It searches and analyzes information across the board to present a comprehensive, detailed picture of files and events in a single interface.
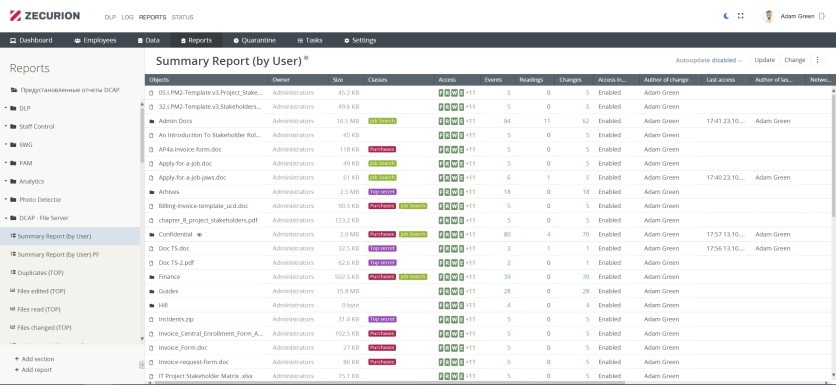
Zecurion DCAP uses policies and reports from the Next Generation DLP to detect shadow data. It identifies policy violations and hidden storage of critical data, which can be used for forensic investigations. The solution offers data protection along with detailed file lifecycle and access management information.
Zecurion Next Generation DLP and DCAP work together as an Insider Threat Prevention Ecosystem to proactively identify and mitigate insider risks. These solutions provide features for monitoring user behavior, detecting anomalies, and preventing unauthorized data access, contributing to a safer and more secure business environment.
Features
Staff Control
Zecurion offers a Staff Control module that provides detailed insights into workforce productivity. It can monitor working hours and log employee actions to ensure compliance with corporate standards and safety policies. It also includes a report designer with 15 indicators, allowing administrators to quickly review staff incidents and access detailed employee dossiers.
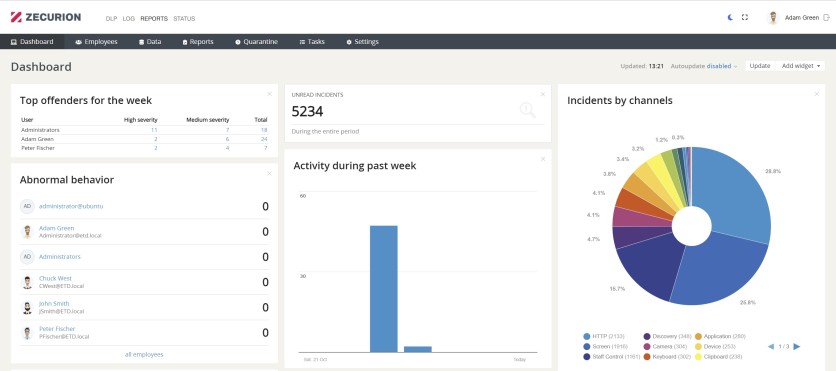
Traffic Control
Zecurion Next Generation DLP monitors traffic and controls the flow of data across 100+ services to minimize the risk of data loss, intentional or accidental.
Device Control
Zecurion ensures a granular approach for data protection through device control. The DLP software can recognize over 500 file formats through its patented preventive content analysis, ensuring confidential and sensitive data is never written to external media.
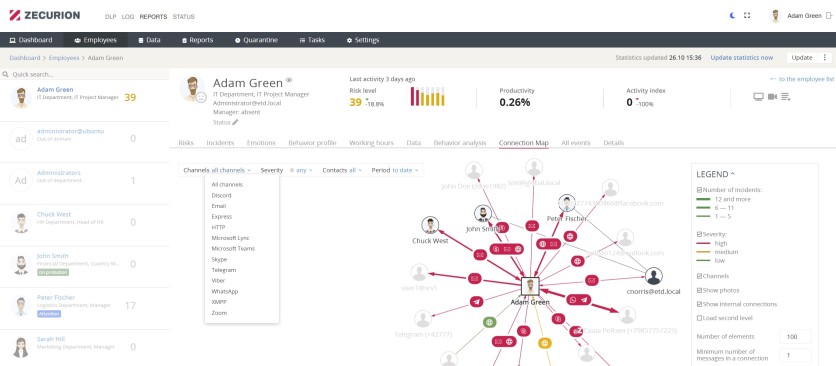
Discovery
Zecurion has the ability to identify sensitive data improperly stored on local drives, shared folders, MS SharePoint, and any data database using ODBC. Companies can ensure that all data stored on endpoints is properly identified and stored through discovery.
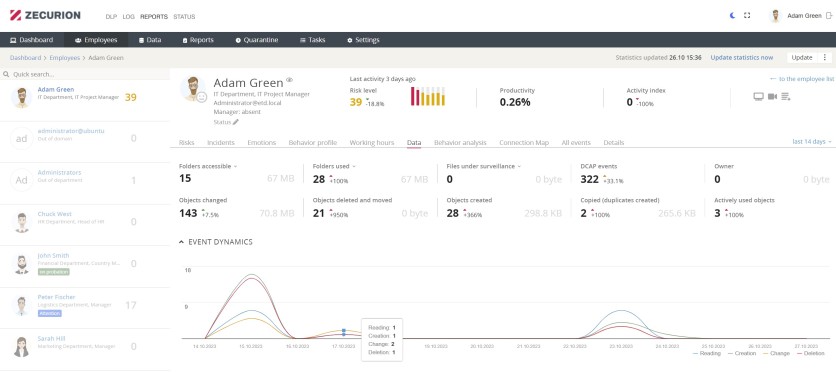
User Behavior Analytics
It uses 15 indicators and emotional profiling to provide user behavior analytics and detect potential insider threats. The DLP software compares current behavior with average values to detect anomalies, helping companies identify and mitigate risks early.
Screen Photo Detector
Zecurion Next Generation DLP can detect and block attempts from users to photograph screens via their smartphones. The DLP software can detect and flag as fast as 0.06 seconds.
Investigation Workflow Automation
Zecurion provides a comprehensive view of tasks with all the statuses, including data on the investigation stage, executants, and deadlines. Investigation workflow automation helps ease the workload of cybersecurity teams since they can see everything at a glance and respond to incidents more promptly.
Video to embed: Zecurion Data Loss Prevention
#2 Symantec DLP

Overview
Symantec DLP Core solution extends data loss prevention across the enterprise. It combines device location, user risk, data discovery, and policies that allow dynamic data access decisions to be taken. The solution gives complete visibility and control over information, as it scans all channels where data passes through and gets stored, from endpoints and cloud apps to network and storage.
The DLP software enforces a single set of policies and workflows that users can manage through a unified web-based console, helping prevent insiders from exfiltrating sensitive data. Since it features integrated User and Entity Behavior Analytics, companies can monitor risky user behavior across control points at all times.
Symantec DLP also boasts remediation capabilities that users can leverage to automate incident response processes like applying policy-based encryption and digital rights to specific files. With its powerful data discovery, monitoring, and protection, companies can use the solution to assess and manage compliance risks.
Analyst firms such as Gartner, Forrester, and IDC recognize Symantec DLP as a proven solution. It reduces the complexity of implementing data protection with a single unified policy framework for detecting and remediating on-premises and cloud-based incidents.
Features
Full Incident Details and Context of Data
Security teams can rapidly investigate incidents and understand data loss risks when they have access to enriched incident data. Symantec DLP provides full incident details and context of data like policies violated, response actions, incident history, and more, speeding up incident response.
Centralized Policies and Granular Controls
Symantec DLP boasts a powerful policy engine that gives admins fine-granted control over how users and applications handle sensitive data. The DLP software can use multiple detection methods for precision, compound matching conditions for accuracy, and group rules and exceptions for individualization. This prevents risky and careless behavior that might lead to accidental data exposure.
Content Detection
Symantec DLP leverages sophisticated detection algorithms and techniques like Exact Data Matching and Sensitive Image Recognition to protect data. It goes beyond regex pattern matching, which can result in high false positive rates.
Advanced Incident Remediation
The DLP software simplifies incident triage and streamlines remediation through its advanced incident remediation capabilities. Symantec DLP automatically responds to incidents as they arise without user intervention. It can enforce actions like escalate, notify, block, and quarantine/restore. Security teams can utilize one-click SmartResponses to intervene when handling more serious incidents.
Real-time Notifications
Real-time notifications can guide users to make smart decisions in handling sensitive data, thus lowering organizational risks. Symantec DLP can educate them on data protection policies as they interact with the data.
#3 Forcepoint ONE Data Security

Overview
Forcepoint ONE Data Security boasts 1700+ predefined classifiers, templates, and policies for powerful enterprise DLP data identification across all major channels, from the web to endpoints, including email. It also has advanced true file type detection that covers 900+ file types.
As a cloud-native DLP solution, Forcepoint ONE Data Security lowers overall spending by eliminating on-prem hardware and software setup costs. Users can create policies with a few clicks and deploy them in minutes. The software provides a unified dashboard where users can monitor incidents, ensuring a comprehensive view of data security across the organization.
Companies can also use the DLP software to automate data based on risky behavior. By integrating with Risk-Adaptive Protection, Forcepoint ONE Data Security facilitates a better understanding of user intent. Deployed on AWS globally, it can easily scale up to 100K+ endpoints and guarantees 99.99% uptime.
Features
Out-of-the-box Compliance Policies
Forcepoint streamlines policy configuration and management with pre-built policies, templates, and classifiers. Companies can leverage these out-of-the-box policies to ensure compliance with privacy regulations in every major global region. The DLP software unifies policy control by letting users deploy a single policy across all egress channels.
NLP Scripts
Forcepoint ONE Data Security leverages natural language processing to identify and secure sensitive information across cloud, web, email, and endpoint. It utilizes 300+ NLP scripts to recognize common data types such as PII, PHI, and PCI based on the described content.
Unified Reporting
The cloud-native DLP solution also unifies reporting across these channels. Forcepoint provides real-time visibility of alerts, with the option to switch between user and incident-based views.
Incident Prioritization
The DLP software displays the top ten actions that require immediate attention. It can also reduce the number of incidents and risk severity when integrated with Risk-Adaptive Protection scoring, which adjusts the deployed policies based on risky user behavior.
#4 Proofpoint

Overview
Proofpoint leverages AI-augmented data classification, user behavior analysis, and threat context to protect data from being lost or mishandled. The platform operates on a cloud-based architecture, which minimizes operational costs and simplifies scaling for large enterprises.
Proofpoint takes a human-centric approach to data loss. The DLP software gathers the contextual clues about who, what, when, and where of the data so users can understand its full lineage, identify baseline activities for the user, and compare them to subsequent actions. It can help organizations contain insider threats and mitigate data loss across multiple channels.
Features
Unified Console
Proofpoint presents a unified console for proactively managing data risks. The platform has sophisticated search and filtering features that users can leverage to discover data exfiltration and risky activities. It provides a timeline view of user activities, making it easier to defend their data against careless, malicious, or compromised users.
Behavioral Visibility
Proofpoint can detect anomalies that may indicate risky activities that could lead to data leaks or breaches. The cloud-based DLP solution uses behavioral AI, CERT institute-based rules, and behavior research to understand user behavior patterns and provide early warnings.
Advanced Content Scanning
Advanced content scanning swiftly identifies and classifies sensitive information across the most critical channels, covering email, cloud applications, endpoint, and web. It can detect when files are being copied to USB devices, synced to cloud sync folders, and uploaded/down to and from web applications.
Granular Privacy Controls
Proofpoint anonymizes user information and masks sensitive content to protect personal data. The platform contains granular privacy controls to ensure analysts only see the data that they need to know.
#5 Coro Cybersecurity

Overview
Coro contains pre-built DLP functions that protect sensitive information from unauthorized access and misuse. It has a growing collection of security modules that feed into one easy-to-use dashboard that can show the security posture of the entire business. Every time a module is added, the platform updates the endpoints automatically based on the rules set by the user.
Features
Permission Management
Coro can prevent unauthorized access and sharing of sensitive information through permission management. The platform contains a module called User Data Governance that lets users define the rights of individuals and groups of employees. Adding permissions ensures legitimate data access only to authorized individuals.
User Monitoring
Coro leverages its data governance capability to monitor users in real-time. It scans all outgoing communications and flags workspace admins any instance when sensitive information has been sent to unauthorized users. The platform can also monitor customized security and business-sensitive data like passwords, certificates, and source code, which also helps reduce the risk of data breaches.
Ticket Management
The DLP software also creates data monitoring tickets to identify when users violate permissions and monitoring policies when handling sensitive information. Tickets contain information about the type of sensitive information that was detected, the user/device responsible for the trigger, and the context of the activity. Admin users can use tickets to identify and respond to security incidents and even improve the policies and procedures for proper data usage.
Conclusion
Cyberthreats threaten organizations that lack effective data loss prevention practices. Data breaches result in financial losses, sabotage the trust of customers, and tarnish the reputation of the company. Choose the best DLP software to safeguard customer information, protect intellectual property, and achieve data visibility.
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




