
Email represents a large attack surface for any organization. From ransomware to phishing and credentials, cybercriminals have found new ways to use email to deliver malicious payloads and breach corporate security. Email-based threats leverage human emotion, which is far more vulnerable to exploits than advanced security equipment. Threat actors can take advantage of this vulnerability and send a well-crafted email message to bypass all expensive infrastructure defenses.
The year IBM Cost of a Data Breach report from 2024 illustrates the necessity for email security. The report indicates that the average cost of a data breach has increased to $4.45 million, 15% higher than the previous three years. The two most common attack vendors were phishing and credential theft. Whether the result of these email attacks is data theft or malware installation on the network, investing in email security can stop users from interacting with a phishing email.
Understanding Email Security
The most effective email security stops messages from being inboxed but avoids interrupting legitimate communication. Inboxing refers to the process of a message being accepted by the recipient's exchange and making it available to the intended recipient. While small businesses may only receive a few hundred emails a day, enterprise businesses, on the other hand, can receive thousands which must be scanned for malicious content. Many of these messages count as spam or phishing. Adopting email security software can differentiate between a legitimate email message and one that needs to be dropped or quarantined.
Free email services like Gmail or Yahoo have spam folders where users can view and reply to spam messages. A spam inbox reduces user interactivity with a malicious attack but lacks the means to stop all email threats. Businesses have potentially millions at risk if employees access these malicious messages.
Small businesses often don't have the security infrastructure to stop malware when a user interacts with malicious messages; hence, preventing these messages from reaching the user's inbox becomes a top priority to protect their data. Fortunately, several email security vendors have options for businesses of all scales. Each one has unique selling points, which can make the difference between a convenient and effective tool and one that needs to be replaced in the future. This article lists the top 5 email security software vendors in 2024 to help you choose.
#1 Trustifi
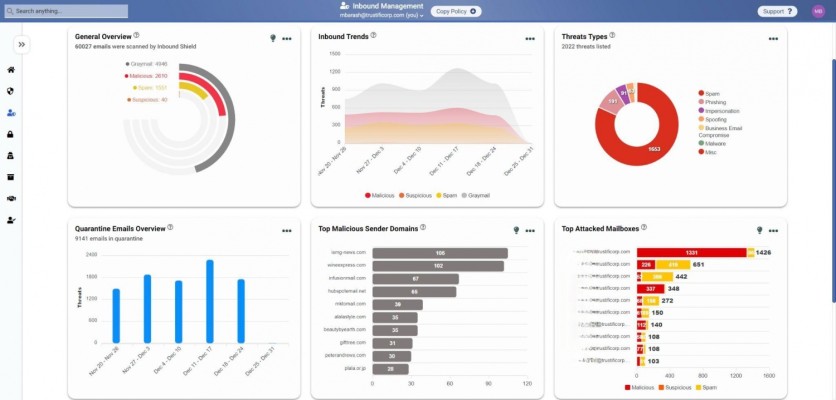
Overview
Convenient and effective, Trustifi boasts superior scanning technology, capable of detecting 99.9% of email-based threats that often evade other email security solutions. Businesses can leverage its artificial intelligence (AI) scanner for pre-delivery email relay technology and post-delivery API scanning. Besides AI-based scanning, this vendor also offers inbound and outbound security scanning in an all-in-one solution: Advanced Inbound Shield and Outbound Shield.
Advanced Inbound protects the environment from incoming malware, phishing, and other email-based threats. Outbound Shield empowers administrators to manage encryption and data privacy for outbound messages containing sensitive information, keeping communications secure and compliant.
Trustifi leverages the power of machine learning and AI to quickly identify and mitigate email-bourne attacks from more routine email threats like viruses and spam to advanced targeted attacks like phishing, CEO impersonation protection, etc., keeping inboxes safe from hackers. It contains more features like account takeover protection, vendor email compromise, email-managed detection and response, and ensuring businesses have robust email security.
Adopting its cloud-based email security platform can protect businesses and data. It supports email services like Gmail and Outlook, wherein its features are integrated with the current email address, so only safe messages arrive in the user's inboxes.
Trustifi also offers security awareness training to help employees identify phishing and social engineering. Businesses can also deploy the platform on-premises. Request a demo or get a quote for a custom security and compliance plan.
Features
Inbound Shield
Inbound Shield leverages AI and dynamic engineers to identify and block suspicious inbound emails. It scans all components of the message from the email body and headers to the links and attachments. Trustifi grants multiple layers of protection to uphold email security, ensuring all potential threats are detected and treated according to admin-specific preferences.
The software vendor gives them access to a proprietary management system where admins can review and take action on quarantined emails received by the users. Admins can also customize inbound rules like blocking specific from/to addresses, auto-forwarding, etc., ensuring bad actors are blocked from users' inboxes.
Outbound Shield
Outbound Shield automatically scans and encrypts outgoing emails according to admin policies, securing the sensitive information enclosed. Without email encryption, threat actors can intercept emails and obtain valuable information.
Trustifi also empowers users to recall email messages, revoke access to attachments, prevent email forwarding, and even create data loss prevention rules, which ensure sensitive information is always sent securely. It offers MFA methods, so only intended recipients have access to the emails that have been sent.
The email security software tracks all emails sent through Postmark so users have real-time knowledge of when and where the email was opened and read, including which files were downloaded or which links were clicked.
Account Takeover Protection
Trustifi can also automatically block access to compromised accounts through account takeover protection. The email security software identifies by tracking the changes in the user's environment, used devices, and other metrics that indicate an email account has been compromised.
It looks out for any suspicious behavior that implies a hacker has penetrated the firewall and taken over the account. It notifies the system admin so they can swiftly analyze the situation and boot out the sessions of the identified account.
Advanced Cloud Email Archiving
Businesses can store data for an unlimited time through archiving. Trustifi offers a secure and convenient way to archive emails on the cloud where users can restore emails after they were deleted and determine the period an email can be retained before getting deleted permanently. It boasts powerful search capabilities and bank-level encryption.
Email Managed Detection and Response
The software vendor can provide a dedicated expert email security team for mitigating risks related to email threats. This service can benefit organizations without experienced security personnel or have multiple IT priorities to manage. The dedicated team becomes an extension of the in-house team to decrease response times to incidents, prevent intrusion of all email attacks, etc.
#2 Abnormal
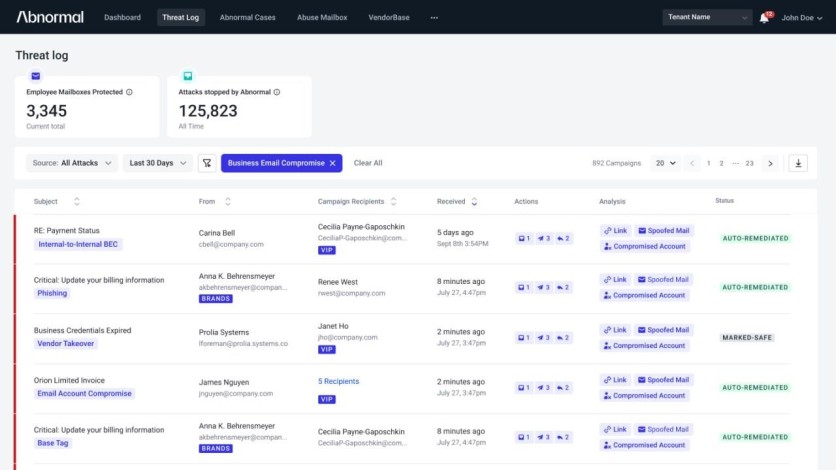
Overview
Abnormal identifies many threats but mainly focuses on inbound email messages. It offers similar inbound scanning features and technology as other email security vendors but lacks other components included to implement holistic email threat protection like data loss protection, encryption, and archiving. The platform integrates via API with Microsoft 365 and its associated apps, Google Workspace, Slack, Zoom, etc.
The cloud-based email security platform provides the visibility and control security analysts need to investigate and remediate threats. Abnormal displays anomalous behavior and activity on its Knowledge Bases where they can derive insights. The AppBase, in particular, displays a list of applications integrated into the environment and lets admins view user permissions through the PeopleBase dashboard.
Abnormal boasts many features to oversee activity in the environment, but its solutions are excluded from the core product. Customers must purchase the add-ons, which may be costly for small businesses, to have unprecedented email protection against the most advanced email threats.
Features
Inbound Email Security
Abnormal can detect anomalies in inbound email messages by analyzing thousands of unique signals. The email security platform remediates the malicious messages, eliminating the possibility of end-user engagement that could expose the network. It provides searchable logs for every message categorized. Admins can check the Threat Log to review trends, learn more about the attacks, and remediate misdirected messages.
AI Security Mailbox
Abnormal utilizes AI to automate user-reported email workflows. For every employee-reported email, it provides remediation action and detailed explanations of whether the email received is safe or malicious according to enterprise security best practices.
The AI security mailbox analyzes, classifies, and remediates all related malicious phishing emails across multiple tenants. It also integrates with existing workflows and SIEM/SOAR solutions, resulting in a centralized alert system for SOC analysts.
Graymail Detection
The email security platform can also identify graymail with high accuracy. Abnormal instantly moves the graymail out of the employee's inbox into a dedicated folder, eliminating the need to create filtering rules or manage blocklists and allowlists.
Email Security across Collaboration Apps
The most popular collaboration apps lack robust security scanning. Abnormal can detect malicious content across these apps and display them in the Threat Log. This add-on scans all internal and external messaging threats to detect insider threats and reduce the risk of supply chain attacks.
#3 Proofpoint
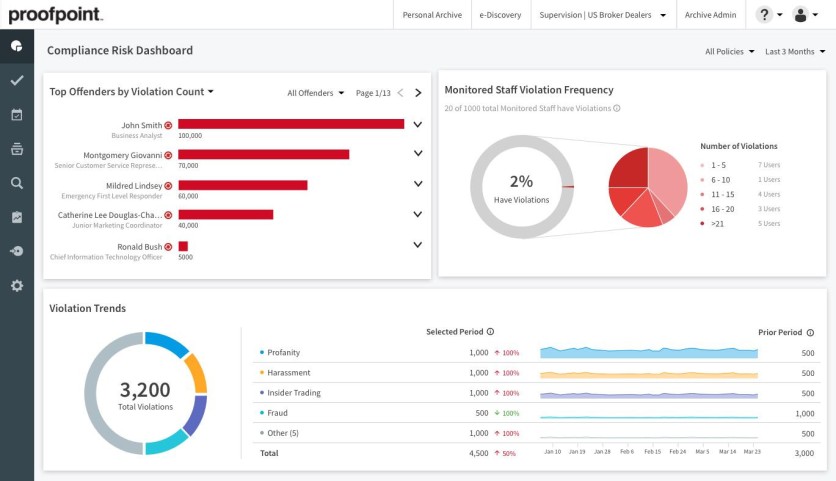
Overview
Proofpoint offers various solutions for monitoring, threat detection, user behavior benchmarking, identity protection, and operational support. It can catch both known and unknown threats that other software solutions miss. However, it has difficulty detecting AI-based email threats.
The software vendor offers threat protection solution bundles with flexible deployment options (on or off-premises). The email security software helps secure and control inbound and outbound email as it gives granular control over various types of email, including imposter email, phishing, malware, bulk mail, etc. It also automatically tags suspicious emails so users can report directly from the tag.
Features
Advanced BEC Defense
Powered by NexusAI, Advanced BEC Defense is designed to find and stop BEC (business email compromise) attacks. It detects them by analyzing message attributes such as message header data, sender's IP address, and message body. Proofpoint also provides granular visibility into BEC threat details and observations of why a message is suspicious.
Multilayered Detection Techniques
Proofpoint integrates multilayered detection techniques into its software like signature-based detection to block threats like viruses, trojan horses, and ransomware. It also utilizes dynamic reputation analysis to assess local and global IP addresses to determine if an email connection is safe to accept. The email security software quarantines incoming emails by type and classifies a wide variety of emails. These techniques protect businesses by detecting the first signs of malicious activity.
Smart Search
Proofpoint boasts a powerful search capability that lets users easily pinpoint hard-to-find log data so they can trace where emails come from and go. It can down any email in seconds. It provides granular details of search results, including metadata with 100+ attributes. Moreover, it contains several real-time reports so businesses have visibility into mail flow and trends and a basis to address issues as they emerge.
#4 Mimecast
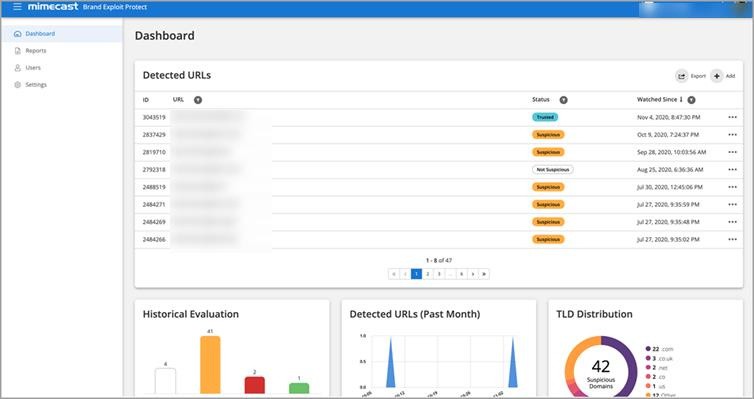
Overview
Mimecast leverages AI to block email-based threats of any complexity. It conducts real-time threat analysis and filtering for email protection. Deficiencies, however, exist in its inbound scanning technology as AI-based email threats can bypass its filters, which can lead to false negatives.
Using this email security software entails a huge learning curve, making it difficult for users to get up to speed on its features. Despite this downside, Mimecast remains effective in eliminating spam, bulk phishing emails, and impersonation attacks. This software vendor also offers data protection, security awareness training, and cloud archives. Businesses can deploy this solution with or without a gateway.
Features
Comprehensive Protection
Businesses can remove threats even before emails are opened when using Mimecast. The email security software can address relentless phishing attacks with its real-time threat analysis and filtering. It can also defend businesses against malware threats, BEC, and impersonation attacks. It provides complete visibility into the impersonator, helping protect a company's domain from spoofing attacks. It can deter frauds who intend to ruin a company's reputation.
QR Code Defense
Mimecast also blocks quishing (QR code phishing attacks) with its QR code detection and deep URL scanning. These email attacks exploit the trust users place in emails. The email security software can determine malicious intent by leveraging AI to identify and block QR code scams.
Integrated Email Intelligence
Mimecast boasts over 250 partner integrations to enhance detections and enable threat sharing. Businesses can leverage integrations to expand the coverage and functionality of the email security software like using CipherMail for automatic encryption or RSA for automated identity intelligence.
#5 Barracuda

Overview
Known for its network protection, Barracuda can also protect businesses against email-based threats. It leverages machine learning to achieve a high level of accuracy for threat detection. This email security software specializes in blocking nuisance messages. Businesses with spam problems can utilize this solution for its excellent spam protection.
Features
Advanced Threat Protection
Barracuda combines behavioral, heuristic, and sandboxing technologies to implement advanced threat protection against zero-hour and targeted attacks. It automatically scans email attachments in real-time wherein suspicious attachments get detonated in a sandbox environment to observe their behavior. This email security software also leverages industry-leading techniques to scan email messages like spam scoring, URL link protection, reputation checks, etc.
Domain Fraud Protection
Barracuda can also prevent email domain fraud through DMARC (Domain-based Message Authentication, Reporting & Conformance) reporting and analysis. It gives visibility into legitimate and non-legitimate emails being sent with a particular domain so users can make sure their emails are delivered correctly. The email security software can increase their legitimate email deliverability by ensuring the emails pass email authentication.
Incident Response
Barracuda empowers users with fully automated, post-delivery incident response and threat-hunting capabilities to locate threats present in their inboxes. It can also identify users who received and interacted with malicious emails. It automatically sends them instructions to change their passwords and other actions necessary for remediation.
Risks and Challenges in Email Security
No business wants interruptions in communication, so choosing the email security software with the lowest false positive rate can lessen the risks of falling victim to email-based threats. A false positive blocks legitimate communication from reaching a recipient, which can result in loss of revenue and brand reputation damage.
Opposite to false positives are false negatives. False negatives allow malicious messages to reach the recipient's inbox, which means a software vendor with a high false negative rate renders its solution useless. Businesses must find an application that offers a high rate of success and true positives.
Implementation and Best Practices
Every vendor should offer instructions on implementation and configuration, but most email security software strives to make it as simple as possible for their customers. Most vendors grant the option to deploy their solution in the cloud or on-premises, but the most convenient is deployment using an MX record wherein the email is scanned prior to being stored in the exchange. Only after an email scan does the email reach the recipient inboxes.
Most vendors also offer a deployment dashboard available in a web browser. Administrators can deploy the solution with an MX change and configurations available in the dashboard. Configurations for user permissions and outbound DLP scan messages for any sensitive data, but administrators must configure any exceptions and if email security should block the message or automatically encrypt and send. Also, configurations for quarantined messages tell the software to drop messages or save them for further review.
For larger businesses, a good email security vendor lets them upload a list of users from a CSV file. Administrators can export users from their identity management tool and import it into the email application. The list of users can then be used to configure groups and determine rules for scanned messages. For example, a security engineer might need access to quarantined messages, but a customer service agent should not receive any suspicious messages.
Measuring the Effectiveness of Your Email Security
Stakeholders want to know that their security budget protects assets and is worth the costs. Email security vendors offer reports and snapshots of several metrics. Metrics include the number of phishing emails blocked, users commonly targeted, reporting features for users and administrators to alert the vendor, incident types detected, domains with common incidents, devices accessing email, and locations of users.
Metrics can be used in budget reporting and board presentations. They can also be used by small businesses to review the effectiveness of their security budgets. Every attack blocked lowers the risks of a potential data breach, so it saves from the revenue impact of a data breach and the long-term costs associated with brand reputation damage and a loss in customer trust.
Choosing the Right Email Security
There are factors to consider, besides the success rate, before investing in a software solution. Businesses must also consider the key features, pricing, if technical support is included, and whether the solution integrates with third-party apps.
Key Features
When it comes to choosing the right email security solution, businesses must first check if the software has the key features for security to be effective, namely:
● Phishing and malware filters: Whether it's artificial intelligence or homegrown detection software, email security must be able to block 99% of malicious emails.
● Spam filtering: Just like blocking malicious emails, spam is a nuisance that exhausts business storage resources. Email security should include spam filtering.
● Sandboxing: Malicious messages shouldn't be dropped, so administrators can review messages in a quarantine dashboard. Sandboxing blocks malware, but it allows administrators to review activity on the email exchange and security application.
● Data loss prevention (DLP): Effective email security also encrypts and protects sensitive data from being disclosed or misused. Outgoing messages should be scanned for sensitive data and encrypted to prevent disclosure.
Pricing
After finding the email security solution with the right features, businesses must also consider the pricing. Some vendors offer their solutions at an affordable price but charge extra to configure and run the software fit for the business. Ensure the budget covers all the features and the vendor includes them with the license.
Technical Support
Technical support is also critical for businesses, especially during the initial set-up. It is ideal if the vendor can assist with technical issues and configurations when roadblocks are encountered. Check the licensing agreement to ensure support is included and not an added expense.
Third-Party Integrations
For any business working with Google Workspace or Office 365, ensure the software integrates with these common enterprise platforms. It's a mistake to rely solely on native security, so businesses should have an additional layer of email security to stop sophisticated attacks targeting these platforms.
Conclusion
Many organizations rely on email to do business. Without email security, cybercriminals can intercept email messages and gain access to sensitive and confidential information. They risk falling victim to data breaches and suffering long-term results like litigation, revenue loss, and reputational damage when they don't adopt the best email security software. Choose from Trustifi, Abnormal, Proofpoint, Mimecast, and Barracuda to protect mission-critical data and the brand.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




