Europol announced the arrest of four individuals on Thursday and the disruption of over 100 servers in what it described as the largest operation against botnets deploying ransomware.
'Operation Endgame' of Europol Targeting Botnets Deploying Ransomware Leads to Arrest of 4
According to AFP, the "Operation Endgame," led by France, Germany, and the Netherlands, aimed to counter cyber threats ahead of the Paris Olympics. Conducted from May 27 to 29, the operation resulted in four arrests - one in Armenia and three in Ukraine - and included searches in the Netherlands and Portugal.
Targeted servers were also located in countries like Bulgaria, Canada, Germany, Lithuania, Romania, Switzerland, the UK, the US, and Ukraine. Europol also identified eight additional suspects who are now on Europe's Most Wanted list.
One of the arrested persons reportedly gained at least 69 million euros in cryptocurrency by renting out criminal infrastructure to expand ransomware footprint.
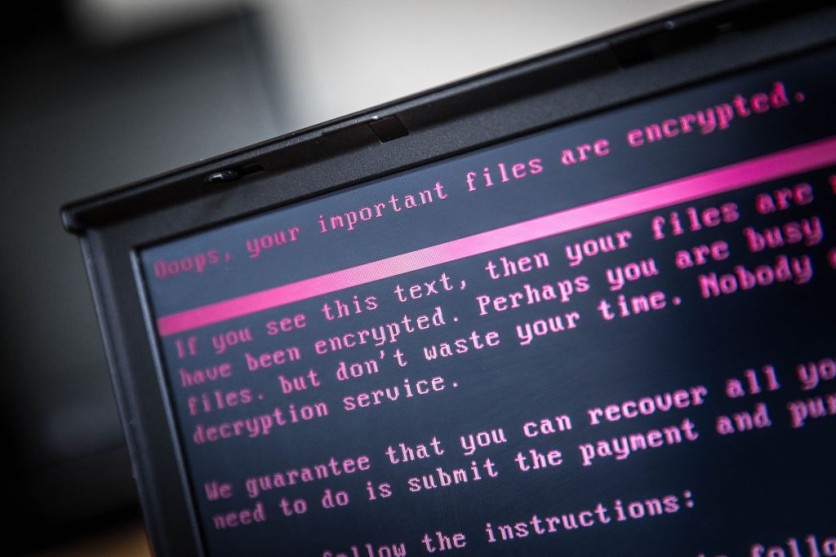
Europol called this the largest operation against botnets, essential for spreading ransomware. Botnets are networks of computers containing malware and controlled remotely by hackers.
The authorities mainly targeted malware "droppers" that insert malicious software into systems. These include IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and Trickbot.
The Trickbot was reportedly used to attack US hospitals during the COVID-19 pandemic. It is also worth noting that droppers help cybercriminals bypass security measures to launch malware such as viruses, ransomware, and spyware.
According to Eurojust, the EU Agency for Criminal Justice Cooperation, malware is typically downloaded via emails with infected links or attachments in Word or PDF formats. Eurojust noted that the operation has only started, with more arrests to come in the future.
Read also: Black Basta Ransomware Attack: Threat Actors Abuse Windows Quick Assist to Launch Phishing Scheme
Weakening Cybercriminals Before the 2024 Olympics
Nicolas Guidoux, head of the French police's cybercrime unit, emphasized the operation's role in weakening cybercriminal infrastructure and limiting resources ahead of the Olympic Games, which is anticipated to be a target for cyberattacks.
Operation Endgame received support from Denmark, Britain, the US, Armenia, Bulgaria, Lithuania, Portugal, Romania, Switzerland, and Ukraine, with the investigation starting in 2022.
German cybercrime prosecutor Benjamin Krause noted that health, education, and public administration sectors were victimized by hackers who encrypted files or entire systems, demanding ransom to unlock them.
French investigators were the ones who discovered the administrators of SystemBC, which enabled anonymous communication between infected systems and command servers, and Pikabot, a Trojan horse known for deploying ransomware and stealing data.
French police also arrested a suspect in Ukraine with local authorization. However, the total victim count will be known after analyzing dismantled servers. According to AFP, experts ultimately believe that the international operation yielded positive results as it destabilized a notoriously difficult criminal ecosystem.
Related Article : Ukrainian REvil Hacker Gets 13 Years in US Prison for His Role in $700M Ransomware Scheme


![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)


