Log data analysis involves reviewing logs generated from different sources to gain insight into the activities of assets in an IT infrastructure. It helps organizations detect and remediate security threats, and meet regulatory requirements.
Wazuh is a free and open source enterprise security platform that offers unified XDR and SIEM capabilities. It aggregates and processes logs in real-time from monitored assets for threat detection and response, ensuring compliance with regulations, and identifying system performance issues, among others. Wazuh offers protection against security threats in the cloud, on-premises, virtualized, and containerized environments.
How Wazuh performs log data analysis
Logs are records of activities generated in real-time by network devices, computer systems, and applications. These generated logs are typically stored in files, and sometimes indexed, or stored in databases for real-time or future analysis.
The Wazuh platform comprises the Wazuh agent and three central components: the Wazuh server, the Wazuh indexer, and the Wazuh dashboard. Wazuh gathers and processes data from a variety of sources in the following way:
The Wazuh agent collects and forwards logs from monitored endpoints to the Wazuh server for processing. It provides threat detection and response for the endpoints on which it is installed. It is multi-platform, supporting Linux/Unix, Windows, macOS, and other operating systems.
The Wazuh server analyzes data received from Wazuh agents and other log sources and triggers alerts when security threats or anomalies are detected. It stores the generated alerts and other events received from monitored endpoints.
The Wazuh indexer stores alerts generated by the Wazuh server in indices and provides near real-time data search and analytics capabilities.
The Wazuh dashboard provides an intuitive web user interface for visualization and query of all data collected and processed across virtualized, on-premises, cloud-based, and containerized environments.
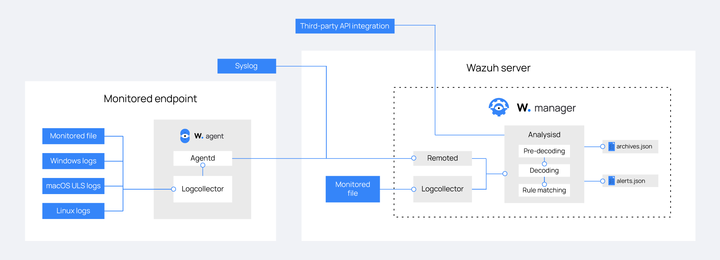
Log data ingestion
Network devices, computer systems, and applications generate logs that can be stored in files. You can configure the Wazuh agent to ingest and forward logs stored in a file to the Wazuh server for analysis. Our documentation shows how the Wazuh agent monitors the contents of files on different operating systems.
Many endpoints, such as firewalls, switches, routers, and other devices, don't support the installation of third-party software. In this scenario, the Wazuh server collects logs from such endpoints using syslog or the Wazuh agentless monitoring capability. You can refer to this documentation to learn how Wazuh uses its agentless monitoring capability to collect logs from endpoints that don't support the installation of agents.
Additionally, the Wazuh server integrates and pulls logs from Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform, and other platforms using external API integrations. These integrations give organizations insight into their cloud workloads and other business platforms.
Log data analysis
Wazuh has predefined decoders and rules to analyze logs from endpoints, firewalls, intrusion prevention systems, routers, switches, and others. These decoders and rules use regular expressions with support for PCRE to process and detect different threat patterns.
Wazuh uses decoders to extract relevant fields from the logs collected. These fields include IP addresses, hostnames, timestamps, usernames, ports, MAC addresses, and other relevant data fields. After Wazuh decodes the collected logs, it compares them against its out-of-the-box rules. When a rule matches a decoded log, alerts are triggered on the Wazuh dashboard.
Wazuh allows users to create custom decoders and rules to analyze logs whose rules and decoders are not included out-of-the-box. In the post, monitoring AWS Managed Microsoft Active Directory with Wazuh, Wazuh uses custom decoders and rules to detect AWS Managed Microsoft Active Directory activities.
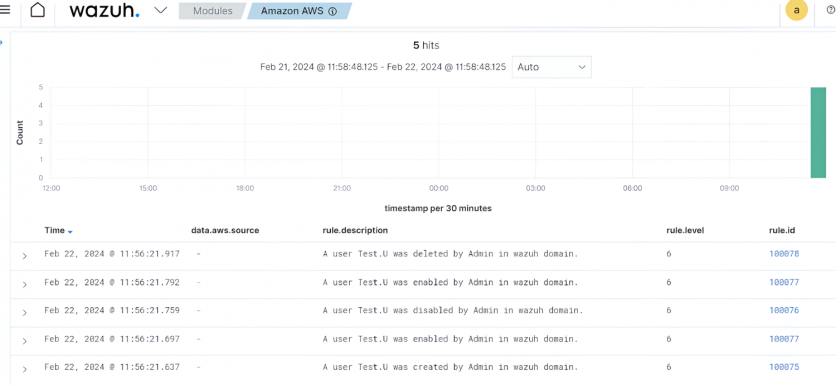
Data visualization
The Wazuh dashboard is a flexible and intuitive user interface. It provides a centralized view of all the data ingested and processed across virtualized, on-premises, cloud-based, and containerized environments.
The Wazuh SIEM and XDR platform provides out-of-the-box dashboards for security events, security configuration assessment, file integrity monitoring, vulnerability detection, and other alerts.
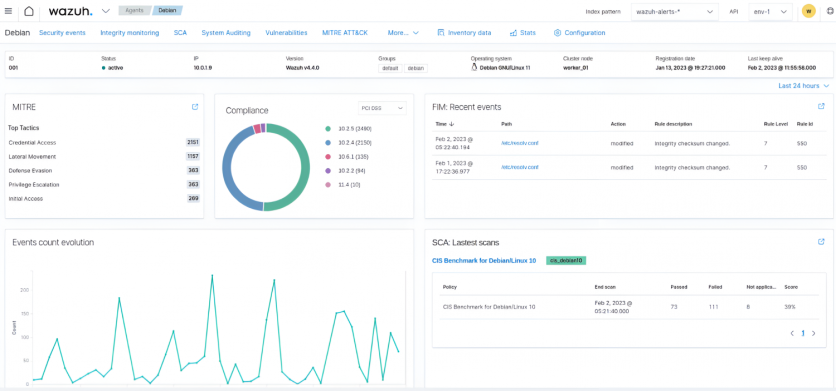
Benefits of using Wazuh for log data analysis
Wazuh performs log data analysis to provide the following benefits to organizations.
Threat detection and response
Digital assets generate logs that are helpful to the security teams to detect and respond to security incidents. Security teams can leverage Wazuh to process asset logs to promptly detect and remediate security incidents like brute force attacks, distributed denial of service (DDoS) attacks, malware infections, and others.
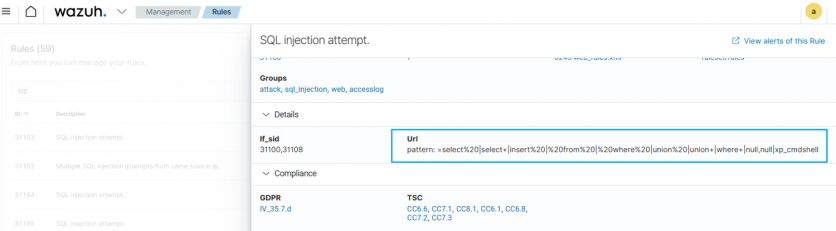
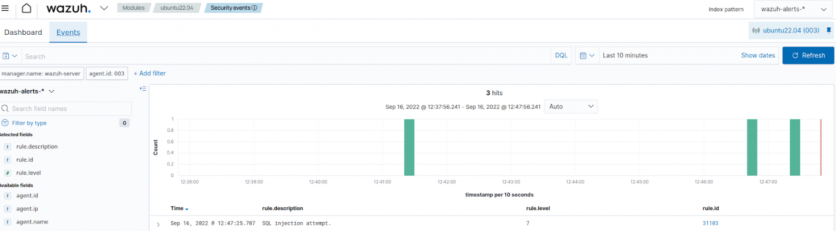
For example, we show how Wazuh detects an SQL injection attack and a Vidar malware infection.
An SQL injection is a cyber attack that allows threat actors to inject malicious code into an application to view or modify its contents. SQL injection attacks have a devastating impact on organizations that handle sensitive information. Wazuh uses the below rule pattern to detect an SQL injection attack against a web application.
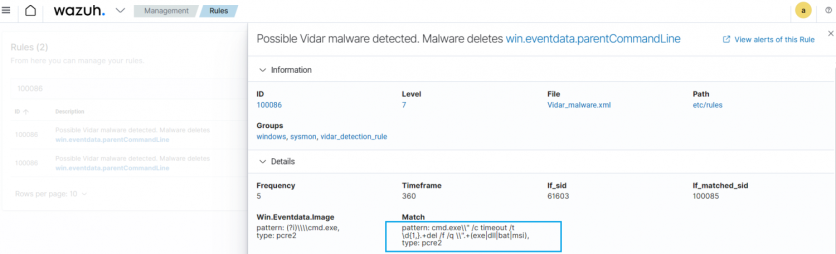
Vidar is a malware that steals sensitive information from cryptocurrency wallets, web browsers, and other applications like WinSCP, Telegram, and Authy 2FA on infected Windows endpoints. Threat actors use legitimate software such as AnyDesk, Notepad++, and others to distribute this malware. The blog post on detecting Vidar infostealer with Wazuh shows how Wazuh detects Vidar malware. One behavior of Vidar is to delete itself or the malicious files it creates from the infected endpoint to evade detection. It runs the following command to execute this behavior:
C:WindowsSystem32cmd.exe /c taskkill /im /f & timeout /t 6 & del /f /q " " & del C:ProgramData*.dll & exit |
The Wazuh rule pattern below detects Vidar's behavior. Wazuh leverages MITRE ATT&CK framework to map different threat patterns to their tactics and techniques. In this scenario, Wazuh maps the defense evasion tactic and T1070.004 technique to Vidar.
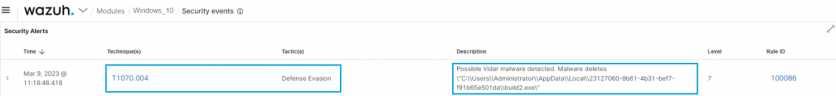
Meeting regulatory compliance
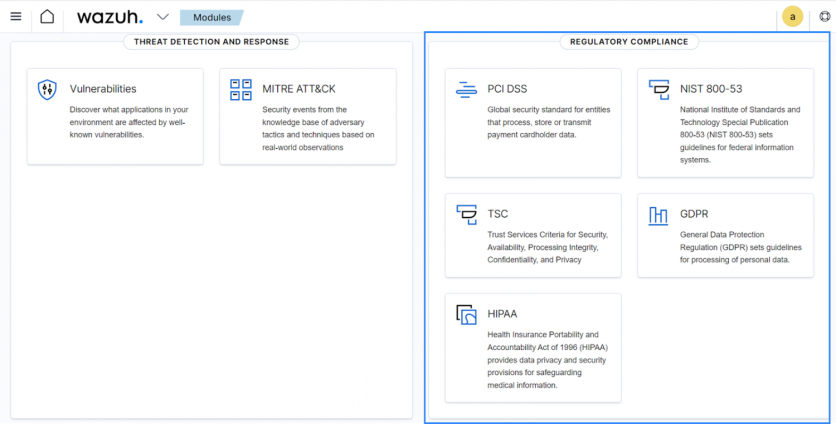
Organizations need to comply with many regulatory requirements depending on the nature of their business. Wazuh assists organizations in meeting compliance with regulatory requirements like CIS benchmarks, NIST 800-53, HIPAA, and PCI DSS by analyzing logs from different assets.
Wazuh provides organizations with capabilities such as security configuration assessment, command monitoring, log data analysis, and others to effectively streamline compliance implementation and maintenance.
Visibility across an IT infrastructure
Wazuh provides holistic insight into an IT infrastructure by performing real-time processing of logs from endpoints and network devices using decoders and rules. This visibility helps organizations in retrieving relevant information from assets and effectively managing applications in their IT infrastructure.
Monitoring system resources
Monitoring system resources like CPU usage, CPU load, memory utilization, and disk usage is crucial to optimizing performance and maintaining the security of an organization's assets. Log data analysis aids organizations in identifying performance issues in their systems and provides clues regarding the root cause.
The Wazuh agent installed on a monitored endpoint uses the Wazuh Syscollector capability to collect system information such as memory usage, number of CPU cores, and others. You can configure the Wazuh agent to gather system information like CPU, memory, and disk utilization. Monitoring macOS resource usage with Wazuh describes how Wazuh monitors macOS system resource usage.

Conclusion
Log data analysis helps organizations detect and respond to security incidents, meet regulatory requirements, and monitor system performance. This post shows how Wazuh provides some capabilities that an organization can leverage to analyze its data for threat detection and response.
Wazuh is a free and open source security solution with capabilities such as security threat detection, incident response, threat intelligence, and others. Wazuh integrates with many third-party platforms to extend its capabilities. Learn more about Wazuh by checking out our documentation, and joining our community of professionals.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




