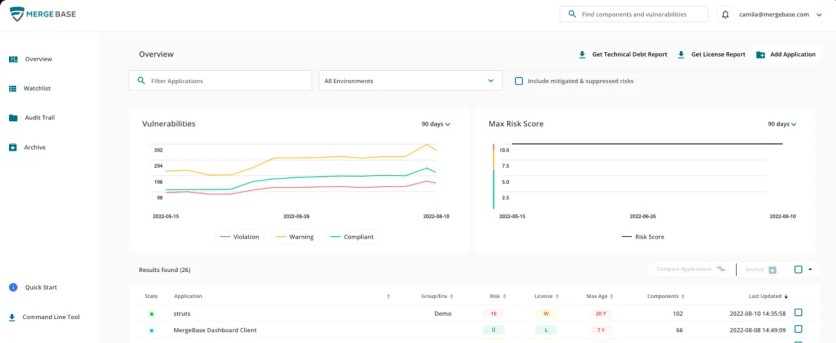
In recent years, cyberattacks on software supply chains have surged, intensifying the pressure on DevSecOps teams to fortify software applications. With up to 90% of an application's code base comprising third-party libraries, the attack surface is increasingly vulnerable. To tackle this, companies have turned to software composition analysis solutions to minimize exposure to vulnerabilities and efficiently address them.
Meet MergeBase, a software composition analysis tool. It excels at identifying, managing, and securing open-source components and third-party libraries used in software applications. By scanning source code and generating a comprehensive inventory of components, libraries, and dependencies, it equips teams to preemptively secure vulnerabilities, thwarting threat actors before they can exploit any weaknesses.
What is software composition analysis?
SCA is the key to unearthing vulnerabilities and licenses in dependencies, ensuring software providers establish and maintain secure codebases. It's a lifeline that alerts teams to issues within scanned components and offers actionable solutions. Plus, it provides a panoramic view of the software supply chain, even delving into the libraries upon which your application is built.
As technology advances, so do the strategies of hackers seeking to exploit businesses and their resources, from systems to applications. In this landscape, there's no room for complacency when it comes to security vulnerabilities. Luckily, SCA tools like MergeBase are here to maintain control over vulnerabilities, curtail security costs, avert data breaches, and instill developers with the confidence to build and ship code securely.
Features of MergeBase
MergeBase is recommended for anyone who makes or uses software in their business process, especially companies that are dependent on enterprise applications. It provides software supply chain protection by detecting vulnerabilities, identifying legal issues, and reducing the costs of maintenance or repair. It also accelerates product development through auto-patching, guiding developers on the best upgrade path to reduce time to market. Outlined below are the main features of the SCA tool.
Low False Positives
False positives are the bane of security tools. MergeBase has been meticulously crafted for accuracy, offering an incredibly low false positive rate. This precision ensures that it pinpoints and reports vulnerabilities at every stage of the software development life cycle (SDLC).
Low false positives are proven to be vital in ensuring that your teams do not experience patching fatigue that delays software launches. With more time on their hands, they can give their undivided attention to doing productive activities like software development.
Software Bill of Materials
MergeBase empowers the creation and validation of software bills of materials (SBOM). This detailed list encompasses all the components and subcomponents of your software code, fostering a shared understanding between customers and vendors. It holds vendors accountable for sourcing secure third-party code and motivates subcomponent producers to bolster security. With an automated SBOM production via a command-line tool, teams receive updated lists with every software revision, enabling rapid vulnerability resolution.
Dynamic Application Hardening
MergeBase features a patented SCA runtime protection for dynamic application hardening to improve Java security. This feature allows teams to block Java-related Common Vulnerabilities and Exposures (CVEs), be it an entire library or a specific vulnerable function.
This proactive approach reduces the attack surface by closing access to unused third-party libraries and functions, mitigating the operational risks tied to implementing new patches into production. Real-time monitoring of third-party dependencies helps teams stop known exploits, even those unknown or zero-day attacks, breaking the attackers' chain before they can strike.
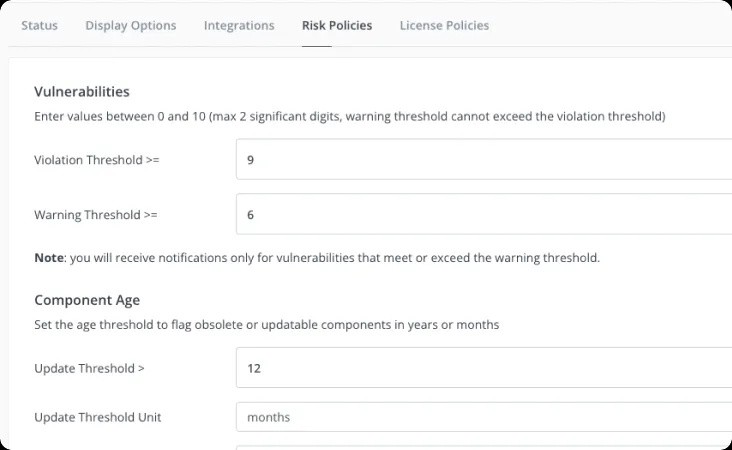
Suppression Management
MergeBase simplifies suppression management, a crucial aspect of managing legal risk and prioritizing vulnerabilities. It conducts a comprehensive analysis of open-source licenses, preventing violations and ensuring compliance with copyright laws. Teams can customize policies to meet legal requirements, becoming more informed in prioritizing vulnerability mitigation and preventing overload.
Easy Integration
MergeBase seamlessly integrates with existing security tools used in your workflows, including GitHub, Jenkins, Docker, Slack, TeamCity, ThreatConnect, and more.
FAQs
Is MergeBase made for applications customers build or those they buy?
MergeBase is a versatile tool suitable for all applications, whether developed in-house or procured from third-party vendors. It excels in monitoring and analyzing vulnerabilities across the entire SDLC, from development to production and operation.
Is having an SCA tool necessary when I already have security tools such as static analyzers, firewalls, intrusion detection systems, pen testing tools, and so on?
While all these tools are critical, they can only find up to 30% of the vulnerabilities a SCA tool can discover. They possess different strengths and weaknesses and cover different areas of cyber security. Their utility complements the solutions MergeBase can offer in strengthening the security of applications.
What languages and environments can MergeBase detect vulnerabilities?
MergeBase can detect vulnerabilities in Java, C/C++, .NET, Python, Javascript, Scala, Ruby, PHP, Elixir, and Go. Also, its patent-pending live protection is available for the Java system.
Conclusion
Start a 14-day free trial and become proactive in identifying and managing risks associated with using open-source components and third-party libraries with a comprehensive SCA solution.MergeBase expedites development, eases the technical burden on your team, and seamlessly integrates with enterprise security information and event management tools. With its comprehensive set of features, it's your ticket to fortifying application security. Don't wait; start your free trial now.
![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)



