
The number of documented supply chain attacks involving malicious third-party components has increased 633% over the past year, and OWASP notes that security misconfigurations, sensitive data exposure, broken access control, under-protected APIs, and using components with known vulnerabilities continue to be top security concerns. That's why today, more than ever, it's critical for modern businesses to implement best-of-breed AppSec tooling.
What Are the Objectives of Application Security?
Protection against digital threats: Companies can utilize application security to safeguard their software applications from various digital threats.
Comprehensive protection throughout development: Application security solutions can be applied at all stages of development, ensuring that the code and data remain protected from the early phases of deployment.
Identifying weaknesses and implementing security measures: Application security aids in identifying vulnerabilities and implementing necessary security measures to protect the confidentiality, integrity, and availability of data and the application.
Prevention of unauthorized access: It helps in preventing unauthorized access to sensitive information and resources.
Data encryption: Application security facilitates data encryption, providing an additional layer of protection against potential vulnerabilities.
In 2023, the following are considered the best application security solutions:
1 Apiiro

Overview
Apiiro's mission is to bring together application risk visibility, prioritization, and remediation through its cutting-edge application security platform. With this platform, security and development teams can confidently ensure that everything they build and deploy to the cloud remains shielded from cyber threats.
Renowned global enterprises have already harnessed the power of Apiiro to take decisive action against critical risks spanning millions of code repositories, pipelines, and development environments.
The core of Apiiro's platform is a single, all-encompassing solution that provides unparalleled visibility into the attack surface of modern cloud applications. Purpose-built for protection and designed to support agile teams, Apiiro empowers proactive security measures throughout the entire application lifecycle, from design to production, including the software supply chain.
The platform's robust capabilities include deep code analysis and runtime context, which enable the identification of vulnerabilities. In real-time, the entire application attack surface is mapped out, presenting a comprehensive inventory of various components, controls, and interconnected elements that may be at risk.

Apiiro further offers detailed insights into Infrastructure-as-Code (IaC) templates, data models, and more based on ticketing systems and runtime environments of both applications and supply chain inventories.
By displaying all this crucial information, developers and security teams alike can easily monitor material changes through a timeline-based history, address current risks promptly, and identify recurring vulnerabilities throughout the development cycle.
A standout feature of Apiiro's platform is the Risk Graph, which uncovers links between risks and attack vectors that often elude other security tools. This enables companies to prioritize risks effectively through security alerts while contextualizing them based on the application architecture and their potential impact on the organization.
Moreover, Apiiro integrates seamlessly with other cloud security tools, consolidating them into a unified platform for enhanced visibility and protection against vulnerabilities.
Features
Application Security Posture Management
Apiiro's application security posture management (ASPM) solves the challenge of securing vulnerabilities without proper context or understanding. By integrating third-party security tools and providing real-time inventory access to code components, Apiiro empowers developers to map the application architecture and identify priority actions based on the application environment and business context.
The automation within ASPM streamlines risk assessment and triggers contextual remediation, allowing developers to focus on the most critical vulnerabilities, ultimately saving time and resources and elevating the overall security and quality of the delivered cloud applications.
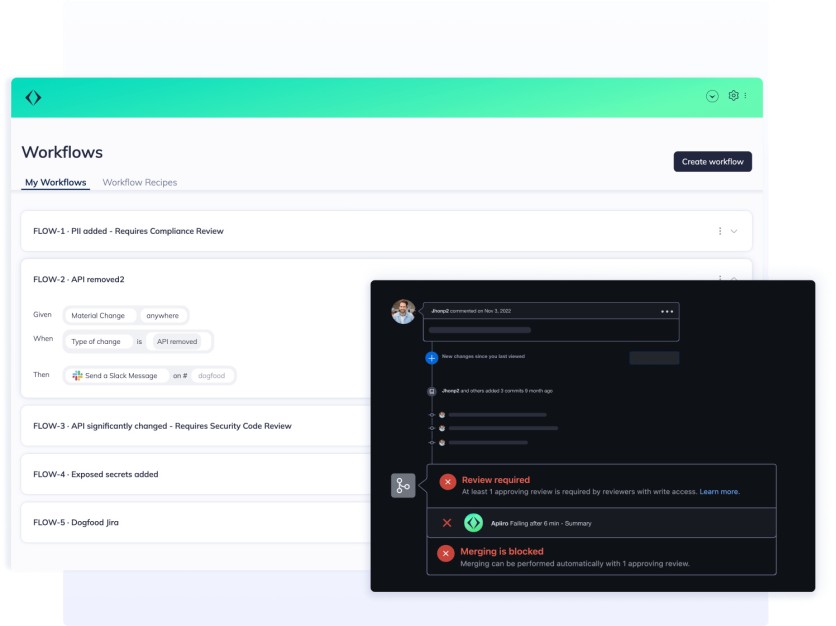
eXtended Software Bill of Materials (XBOM)
Apiiro's eXtended Software Bill of Materials (XBOM) offers comprehensive coverage by presenting a unified inventory of each component, control, data, tool, and process integrated into modern applications and supply chains, along with their interconnections and associated risks.
Going beyond traditional Software Bill of Materials (SBOMs), the graph-based XBOM provides more in-depth information, including entry points, open-source dependencies, confidential information, data management, code structure, Kubernetes services, infrastructure details, and application risk types.
This comprehensive view empowers companies to better understand and assess risks within their complex application and supply chain attack surfaces, allowing them to make informed decisions in application security testing and stay ahead of potential threats.
Contextual Approach to Open-Source Security
Apiiro's platform combines graph-based application analysis with risk-based guardrails and automation, delivering a contextual approach to open-source security. Beyond application and supply chain security, Apiiro offers solutions related to API, infrastructure, secrets security, and software composition analysis.
Apiiro's application security platform offers unparalleled transparency and visibility, making it highly recommended for pinpointing vulnerabilities in modern applications and software supply chains. With its context-rich insights, companies can confidently enhance their application security testing and fortify their defenses against potential cyber threats.
2 Polaris of Synopsys

Overview
Polaris is Synopsys's cloud-based application security platform, built from software composition analysis (SCA) engines and static application security testing (SAST). It offers fast and highly accurate results with multi-type scanning abilities.
It also enables real-time collaboration among security and development teams, empowering them to meet their deadlines on time for launches without losing sight of the risks affecting their enterprise applications.
Features
Equipped with fAST Static, Polaris offers an automated static analysis of all codebases. It automatically highlights the errors or flaws in the code, making it easier for developers and app testers to address them. This application security platform also contains fAST SCA, enabling automated software composition analysis across the development lifecycle.
With its analysis, Polaris can offer insights into the vulnerabilities of open-source dependencies in the software application. And with its expert verification and analysis, the platform can conveniently remove the false positives detected from the SAST scan results and list the findings according to priority for timely remediation.
Given its ease of use, Synopsys enables seamless integration of its application security solution with development and DevOps toolchains to centralize all tools essential in securing vulnerabilities of modern applications.
Developers and app testers also have the option to set customizable rules, enabling Polaris to automate the enforcement of security and risk policies. Overall, Polaris can deliver accurate results in its detection of vulnerabilities.
3 Cycode

Overview
Cycode is built to address vulnerabilities across the software development lifecycle (SDLC). As an application security solution, it can offer complete end-to-end vulnerability identification with context to developers and security teams. It can perform composition analysis on both software and pipeline components. Cycode can map out vulnerable dependency locations, displaying the identified attack vectors for the app testers to remediate quickly.
Features
Cycode offers two solutions for application security testing: Software Composition Analysis (SCA) and Static Application Security Testing (SAST). The SCA focuses on the components of the application. It offers comprehensive scanning and quick remediation of the identified vulnerabilities and license violations.
Moreover, the SCA can secure pipe dependencies from the source code, build files, plugins, IaC templates, etc. It can also identify the path of the vulnerable components and remediate them as soon as they're detected.
Meanwhile, the SAST focuses on code vulnerabilities early in the development of the software. It can scan at a fast speed without disrupting the development of the application. Its Knowledge Graph can provide visibility across the SDLC, enabling developers to easily detect flaws or errors within the code, dependencies, and other application components.
Cycode can support multiple programming languages for application security. Regardless if they're classified as modern or legacy, companies leverage these two solutions from Cycode to implement security measures across all applications. Overall, Cycode is reliable and easy to use. It simplifies application security through its automated scans and fast remediation.
4 Checkmarx One

Overview
Checkmarx offers efficiency for developers through its award-winning application security testing solutions delivered by its platform, Checkmarx One. As a company, it has been recognized as a leader by influential organizations. It received certifications from ISO, EU GDPR, FedRamp, CSA, and SOC, proving it adheres to and upholds the best practices set by the industry.
Checkmarx ensures complete protection from risks and vulnerabilities by making its platform capable of SAST, SCA, SCS, API, and more. It can easily integrate with existing tools and offers in-time learning as developers resolve the detected vulnerabilities.
Features
Checkmarx One can run thousands of scans daily, enabling developers to accelerate their software delivery in time for deployment. It offers high accuracy in detecting vulnerabilities and easy fine-tuning for quick remediation. It also ranks the findings based on their condition, allowing developers to prioritize the most critical vulnerabilities.
As a comprehensive application security solution, Checkmarx One centralizes all findings in one dashboard, ensuring smooth workflow among developers and app testers. It already contains a common set of integrations for initial security. Moreover, developers can simply add or remove local scanning engines to match their respective workloads.
Overall, Checkmarx One is recommended for its credibility in its application security solutions, given its accreditations and its assistance for fast remediation that enables developers to learn as they manage enterprise applications holistically.
5 Snyk

Overview
Snyk aims to empower businesses by helping with fast app development and staying secure through its application security platform. It detects and resolves security issues efficiently in modern applications, from the first line of code up to its delivery in the cloud.
As a platform, it works effortlessly with existing cloud tools and workflows that developers use. With real-time scanning and high-level visibility, Snyk is trusted by millions of developers, those belonging to multinational tech companies like Amazon Web Services and Google.
Features
Snyk offers advanced reporting as one of its application security solutions by visualizing and quantifying the application's security posture. It can simultaneously meet regulations while providing a framework and evidence of the coding process. With its unlimited scanning, developers and security teams can reduce the number of vulnerabilities, eliminating the risk of failure in the deployment of the application.
Snyk can also provide context-driven prioritization, enabling teams to assess risks better and prioritize them based on the level of threat they pose. This allows a better understanding of its potential impact across the SDLC to identify where the risks come from to prevent them from surfacing again.
Snyk also offers quick resolution, enabling teams to fix issues quickly with just a click, boosting productivity and accelerating software application development. Overall, Snyk has been recommended by 85% of developers due to its ease of use and straightforward functions.
Conclusion
Prioritizing application security does not only save time and money but also allows developers to take charge of the process of launching quality applications. Take advantage of these top 5 application security solutions to ensure a well-developed application. These five allow companies to detect vulnerabilities early on in the development stages, preventing issues from arising and securing applications in time for deployment.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




