
Cyber threats loom large over enterprises and institutions containing confidential population information. Hackers take advantage of any vulnerability to access the organization's and its members' data. Often, the information they gathered is exchanged on the Dark Web.
What Is the Dark Web?
The Dark Web refers to the anonymous spaces of the Internet that are mostly inaccessible to the general public. Commonly, it is the place where cybercriminals meet to exchange items illegally. These include forgeries like credit card statements, digital goods like malware, and computer hacking services that allow cybercriminals to penetrate a computer's network system.
Is It Possible to Monitor the Dark Web?
Regardless of the complex systems that hide in the Dark Web, it is possible to monitor it through monitoring tools that track information meant to be encrypted. Dark web monitoring tools detect threats from malicious actors that take advantage of a civilian's private information or an organization's intellectual property.
Fortunately, cybersecurity companies today not only assess the overall security of an organization's digital ecosystem but also offer Dark Web monitoring tools to protect enterprises and institutions. Below are the top 5 cybersecurity companies that provide the best Dark Web monitoring tools in 2023:
1 Resecurity

Resecurity is a global brand in the industry of cybersecurity. Gene Yoo (CEO), a well-known figure in cybersecurity and risk management field, heads the company, along with ex-Microsoft industry veteran Shawn Loveland (COO) and Christian Lees (CTO). With more than 30 years of practice, he founded Resecurity in 2016. He has made it one of the world's most innovative cybersecurity companies to date, with the mission of enabling organizations to combat cyber threats.
Resecurity was also recognized as a leader in Cyber Threat Intelligence (CTI) and External Risk Mitigation and Management Platforms (ERMM) by Frost & Sullivan. The company was named a Gold Winner in multiple categories by Cyber Excellence Awards, including Managed Threat Hunting, Threat Intelligence, and Digital Forensics & Incident Response (DFIR).
The services and platforms of Resecurity focus on the early detection of data breaches and comprehensive protection against risks from malicious actors. In the unfortunate scenario an organization's network has been breached, companies benefit from the Dark Web monitoring tools. Resecurity monitors the tracks of the cyberhackers who successfully infiltrated the system.
Dark Web Monitoring
The two most valuable resources Resecurity have are time and information. As a company, it owns a Big Data repository that contains billions of threat artifacts and Dark Web records. Resecurity also has a team of experts and cyber threat intelligence specialists with a decade's worth of practice in investigation and intelligence gathering.
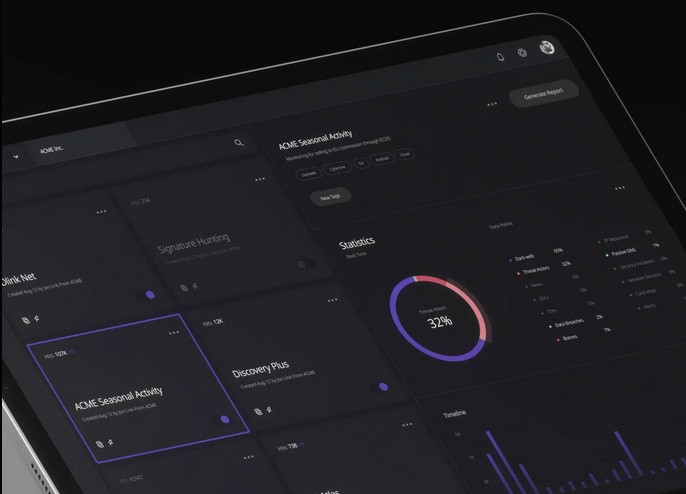
With its Dark Web monitoring tools, companies can automate their digital risk management and receive real-time alerts about security posture changes. These changes may come from unauthorized activities from the Dark Web, data breaches, network infections, and other security incidents.
Resecurity assures that its security measures are accurate for in-depth risk evaluation, expansive to monitor digital footprints on any scale, and effective in enabling actions to improve overall protection.
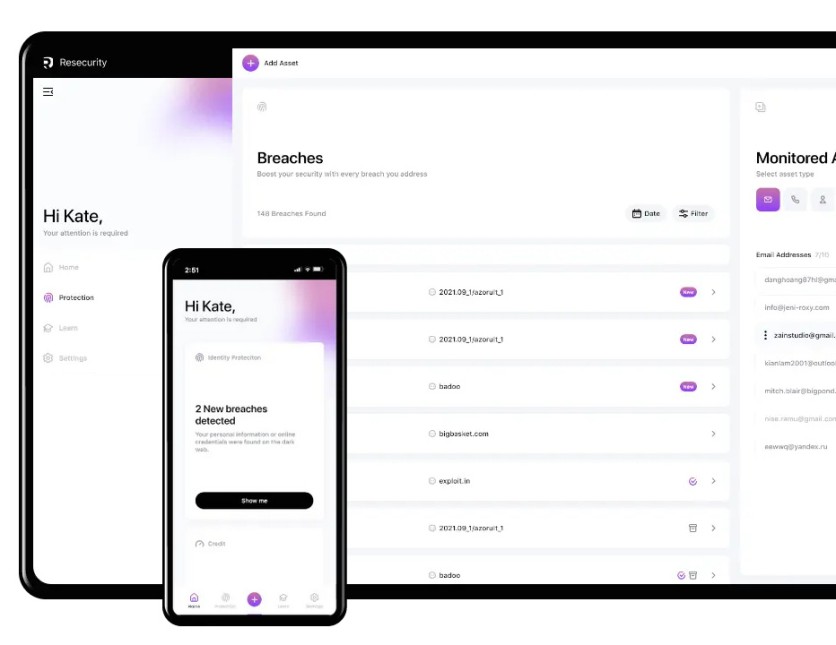
With Resecurity's Risk service, any update of possible threats or the state of a company's cybersecurity is displayed conveniently on a dashboard. Below are its capabilities:
Risk measurement: Resecurity has unparalleled risk management, affording Risk grants companies a daily security score based on all the risks monitored on their domains, IPs, network, vulnerabilities, and cloud services.
Risk assessment: Companies should know where their weaknesses and vulnerabilities lie in their digital assets. The reports provided by Resecurity through its risk assessment can refine and enrich the data points for the company's better understanding.
Risk categories: The service also includes identifying external threats based on the intelligence gathered from over 20,000 public and closed sources that include Dark Web activity, cyber espionage, account takeovers, and other risk vectors.
Global visibility: Resecurity covers all contextual information needed to manage a company's infrastructure, network resources, and other company assets, regardless of location.
Cyber Threat Intelligence
Companies can also leverage the cyber threat intelligence platform of Resecurity called Context. Digital threats continually evolve alongside the speed of technological progress. With Context, companies benefit from its functions through the following:
Monitor the Interweb for possible exposure of sensitive data and confidential documents
Receive updates regarding the activities held in underground communities and marketplaces
Search the farthest spaces of the Internet, including the Dark Web
Intelligence reports from all over the globe
The cyber threat intelligence platform covers different areas of cybersecurity where malicious or threat actors may lurk. Context sets security measures to counter and protect companies like cloud-scale AI, SDK, and API. It aims to counter even the most sophisticated cyber threat, including piracies, fraudulence, and infringements, even in the innermost corners of the Dark Web.
Context draws from multiple sources of the Interweb to combat these threat actors. Government agencies and industry experts have utilized the platform for support due to its comprehensive intelligence gathering and analysis approach.
With the accumulation of 5 billion threat artifacts, 9 million profiles of threat actors, 300 million data entries in the Dark Web, and 20,000 sources in its repository, Resecurity equips organizations and institutions with the most effective tools for combating digital threat and monitoring the virtual spaces that extend to the Dark Web.
2 Flashpoint

Founded in 2010, Flashpoint is a globally trusted leader in risk intelligence. This cybersecurity company possesses industry-leading software that rapidly identifies and remediates the most sophisticated security risks of enterprises and mid-market companies. Flashpoint aims to help organizations by protecting their companies' assets and resources from harm.
Since it was established, Flashpoint has sourced 293 thousand vulnerabilities, 38 billion compromised credentials, 1.9 billion stolen credit cards, 513 million illicit forum posts, and 2.5 billion chat service messages. These numbers prove the credibility of Flashpoint as one of the most trusted companies when it comes to managing risks and intelligence.
Flashpoint's team consists of best-in-class analysts that utilize advanced technology to provide comprehensive coverage of threatening activity on the Internet, starting from the surface web through the deep web and down to the hidden spaces of the Dark Web.
The company works closely with private and public organizations to get ahead of threat actors, reduce their exposure, and drive their ROI up to 5x.
With its Cyber Threat Intelligence solution, companies can benefit from Flashpoint's platform through the following:
understand how threat actors operate to prevent potential targeted attacks
stop ransomware attacks before they happen
monitor employee credentials and confidential information
gain contextual intelligence to identify and remediate vulnerabilities
Companies have witnessed a significant reduction in time, data losses, and exposure when utilizing the products and solutions of Flashpoint. This top cybersecurity company can provide actionable intelligence with the best monitoring tools through its Ignite Platform, regardless of the sector the organization belongs to.
3 SpyCloud

SpyCloud specializes in processing, breaking, and analyzing vast amounts of raw data into actionable results. The company refers to this as cybercrime analytics. This cyber security company focuses mostly on recapturing data from the deepest layers of the Dark Web. With its dark monitoring tool, the Cyber Analytics Engine, SpyCloud possesses more than 12 billion assets per month, collected from data breaches and extracted from malware-infected devices.
SpyCloud's Cyber Analytics Engine processes the collected data. It transforms it into actionable insights that allow companies to identify legitimate users from potential criminals and take action against them to prevent unauthorized activities from happening.
The function of the Cyber Analytics Engine goes beyond data collection. Each digital asset is acquired through a rigorous quality control process to determine its value. Afterward, the team of SpyCloud cleanses, decrypts, and then matches the information to its corresponding users to assess the actual risks it holds against an enterprise.
Companies can then integrate the insights generated by the engine and integrate them into their existing cyber security system to shut down cyber-attacks that match the sources and intelligence of SpyCloud's Cyber Analytics Engine.
SpyCloud takes pride in the 2 billion employees and consumer accounts the company has protected that belong to the most prominent businesses and consumer brands. This qualifies SpyCloud as one of the top cybersecurity companies with the industry's best Dark Web monitoring tools.
4 Ontic

Ontic is an award-winning intelligence software company that transforms the threat management of Fortune 500 and emerging enterprises. In 2021, the company earned the title of the Top Industry Innovator from a program conducted by Frost & Sullivan. In the following year, Ontic earned another award called Global Entrepreneurial Company of the Year. This establishes Ontic as one of the top cybersecurity companies today.
The Protective Intelligence Platform of Ontic functions as a cloud-based solution that unifies real-time and historical data for companies to become proactive in their approach to security. This platform offers a comprehensive view of potential threats while providing companies with critical knowledge to assess and take action against these threats.
Using Ontic's Protective Intelligence Platform, companies can maintain business continuity, reduce financial impact, and protect their employees from potential takeover, fraud, or ransomware. Ontic's platform covers every stage crucial in threat management. It enables companies to identify, investigate, assess, watch, and get notified about threat actors that are invisible to the security measures of their cyber security system.
The platform can detect known and unknown threat actors from various sources, even sources that stem from the Dark Web. When detected, companies get automated real-time alerts that enable them to act more efficiently to protect their employees, organization, and, most importantly, their bottom line.
5 Recorded Future

Founded in 2007, Recorded Future is one of the world's largest intelligence companies. While the company only integrated open and Dark Web sourcing in 2014, the company has come a long way, with 1,500+ clients, nearly a thousand employees, over $200 million, and the world's largest holdings of interconnected threat data. Recently, the company even launched the world's first AI for intelligence.
Recorded Future has an intelligence cloud platform that expands into four channels that track, monitor, and alert companies of cyber threats from vectors like the Dark Web. The underground sites of the Dark Web are sources of intelligence that Recorded Future's platform can process and from which create links to other threat sources. The platform then alerts companies which allows them to mitigate the potential risks these threats can cause to their organization.
Companies can benefit from Recorded Future's Dark Web monitoring through the following:
Automate the identification of proprietary data or lost credentials related to the organization
Uncover new and emerging exploits and malicious codes
Prioritize remediation efforts based on the evidence of the adversary
Continuously receive new high-value Dark Web sources
With the creation of Intelligence Graph, an extension of the company's intelligence cloud platform, Recorded Future can collect, structure, and analyze threat data from all over the Internet, turn them into actionable insights, and deliver comprehensive, relevant, and accurate intelligence for organizations worldwide.
Each company listed above offers a unique yet comprehensive set of the best Dark Web monitoring tools for organizations to improve their threat management. Choose among these top 5 cybersecurity companies that specialize in intelligence gathering, Dark Web monitoring, and enforcing high-level security systems for protection in the ever-changing digital landscape of the Interweb.
Read more: Top 5 Best Dark Web Monitoring Tools in 2022
![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)



