Penetration testing, more commonly shortened to pen testing, is a quick and common method for brands to ensure that user or business data is safely secured from potential bad actors.
According to Statista, an estimated 1,802 cases of data compromises occurred in 2022 in the U.S. alone. Meanwhile, a staggering 422 million individuals were affected by these breaches, showcasing how rampant the problem is and how vulnerable some of the most advanced protection can be when left unchecked.
Pen Testing Service and Its Importance

Pen-Testing-as-a-Service (PTaaS) is a relatively new concept that provides businesses with a more accessible and cost-effective way to determine possible vulnerabilities that could be present on their systems, network, software, or infrastructure.
It is important to note that there are different kinds of pen testing from the many companies that provide such services. Penetration testing can be done manually or through automated tools, depending on who offers it.
That being said, penetration testing is one of the surefire ways to identify vulnerabilities and weaknesses in a company's security system before a real cyber-attack occurs. A successful cyber-attack can have devastating consequences, including financial loss, reputational damage, and legal repercussions.
While this may be a case of "prevention is better than cure," even security specialists may think that they are set with what they have, only to find out later that threat actors have already located a possible entry point and damaged the system long before its discovery.
Thus, it is crucial now more than ever to maintain better protective measures over business software and sensitive client information. Below are our top five reasons businesses must prioritize their cybersecurity tech stack with pen testing providers, like BreachLock.
Why Should You Choose Pen Testing as a Service?
1. Lower Recovery Expenses
The foremost reason is to prevent expensive breaches. You would not want to pay regulatory fines due to a security incident you can report. A ransomware attack may occur simply because prior pen testing was not conducted. The money you unwillingly put forward to fix post-breach problems could have been leveraged by a trusted provider for highly advanced pen testing, instead.
According to IBM Security, the average data breach cost in 2022 was $4.35 million, a 2.6% increase over 2021 (previously $4.24 million). The report also highlights that system errors were proven to be the highest growing issue, seeing an increase of $480,000.
Internal system reliability is paramount for daily business workflows and customers' peace of mind. With better protection and ample resources for preventing cyber attacks, you will save money in the long term and avoid preventable breaches that result in losing customers.
2. Strengthen Governance Procedures
When buying into the necessity for a pen testing provider, you will be actively strengthening your current cybersecurity stack via their services. There might be some powerful security infrastructure keeping your business safe and secure, but you won't know how genuinely secure it is until the inevitable occurs. With pen testing as a service, you can proactively protect your business and your client's data from harm with sophisticated support, including varied attack vector protection, increased vigilance, and even red teaming services.
Red teaming services like those provided by BreachLock allow businesses to improve their systems and security outcomes proactively. These red team exercises include cloud pen testing, application penetration testing, API security tests, and incident response tests to ensure the organization is prepared to respond in the event of a cyber attack. Red teaming takes a more holistic, system-based view of the environment to reveal potential vectors that could lead to a security incident or preventable breach. After red team exercises are done, the in-house team can focus on the remediation guidance from the red teaming services provider and improve cyber resilience with fast patching of vulnerabilities and mitigating attack paths.
3. Stop Preventable Breaches
The obvious is clear with pen testing services and red teaming services. Your business will have a far more robust and reliable cybersecurity system and an overall environment. Through pen testing and rigorous evaluation, you can address any potential flaw in your code, procedure, or infrastructure, as pen testing leverages the very same attack types and vectors that cybercriminals use. This helps in-house teams understand the best way to fix weaknesses in a business' security program.
This isn't a one-time procedure, either. BreachLock's service leverages a four-step plan and 24-hour onboarding process to initialize and actuate advanced penetration testing through a secure, cloud-native pen testing platform.
Following a complete penetration test, BreachLock uniquely integrates remediation early in the pen testing process. This gives businesses the time to conduct their remediation process and complete their pen tests on time. After 90 days from these results, the team can retest vulnerabilities again for any new or still-lingering vulnerabilities using the BreachLock client portal.
4. Compliance with Regulated Data
Though not strictly necessary for everyone, some businesses, like financial ones, require specific security and compliance testing to secure sensitive and private information. These can often include pen testing or red teaming to protect data. When not accurately followed, hampered protection methods could lead to fines.
Pen testing requires ample knowledge of cybersecurity parameters, but not everyone understands the ecosystem. BreachLock's pen testing services feature human-led engagements with in-house, certified pen testers that will ensure data is kept secured and that your system complies with current regulatory requirements. Not all pen testing companies offer in-house, certified experts. It's important to know one's compliance regulations before selecting a pen test provider, since compliance requirements have specific requirements for who can conduct compliance pen testing, like PCI DSS penetration testing.
5. Build Customer Trust
With a trusted pen testing services provider on your side, clients can protect their systems to ensure assets and systems are continuously secured and monitored. With better protective measures and more ways of unearthing and preventing breaches, clients can rest assured that you have secured their sensitive data and private information used in their business.
Data breaches are a significant concern for consumers today. Privacy, too, is of utmost importance. Leveraging sophisticated pen testing and red teaming for your clients is a functional activity that offers proactive protection of regulated data and security testing of company code and IT systems, like external and internal network pen testing, application pen testing, and IoT pen testing.
Why You Should Hire a Pen Testing Service Now
One reason to know before hiring a pen testing service is that it employs "ethical hackers," a.k.a. White-hat hackers, who are designated members of the team. They infiltrate one's services after significant steps to identify a vulnerability and determine where the business or system needs to improve for further protection.
While it is already established to be an essential step in protecting one's systems, choosing the right company may be a crucial factor in getting the best service for you.

BreachLock is a globally renowned leader offering pen testing services, as well as red-teaming, among many features and capabilities that would help contribute to your offensive security requirements.
The company prides itself on its cloud-based security platform. Its Penetration Testing services cover different aspects of one's company, including web applications, networks, the Internet of Things (IoTs), the Cloud, devices, and mobile applications.
BreachLock's pen testing feats have already completed over 8,000 tests in the industry, having reported more than 100 CVEs.
BreachLock's PTaaS: the Four-Step Process
Onboarding - the first part of the service centers on preparing the company's system for the technology that BreachLock will use in 24 hours. Users may access the SaaS platform to be updated and learn more about the process.
Execution - BreachLock executes the penetration testing with a hybrid approach, first using its AI-powered system, then deploying its team members for a more detailed approach. It can deliver results within 5 to 10 business days.
Remediation - Upon getting the report, this would be the time for clients to address the vulnerabilities with the detailed report from BreachLock. They may also re-run the automated PTaaS tests unlimitedly.
Re-evaluation - After the remediation procedure, BreachLock will provide another manual test to update clients regarding the steps they took in addressing the vulnerabilities, with an updated report.
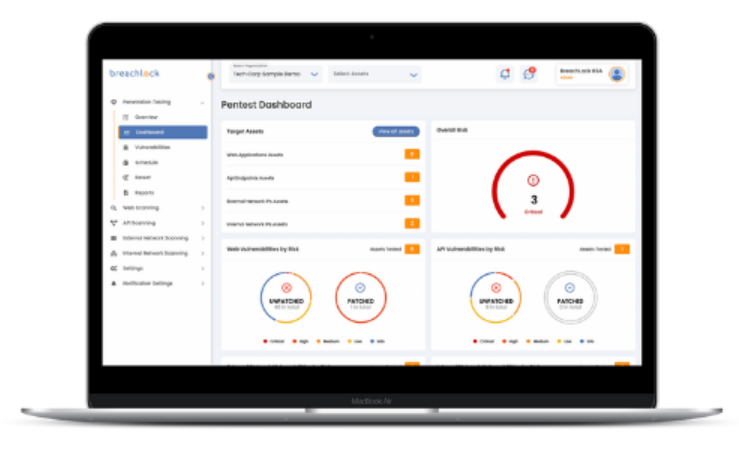
Automated vulnerability discovery methods are a massive part of its pen testing, but the company also offers manual tests that follow up with continuous scanning for a well-rounded report that identifies all possible weaknesses in the system. It also provides further information after the completed test, where its cloud-based SaaS platform offers support and assistance for all client requests.
The platform offers real-time visibility of what is happening throughout the process, giving users a holistic view of the full-stack penetration testing and what needs to be improved.
Schedule a discovery call with BreachLock to learn more about its pricing, plans, and the help they can contribute to improve your security measures for further protection and safety.
Conclusion
Pen-testing-as-a-service is an effective way for companies to identify and address vulnerabilities in their digital infrastructure.
Regular pen testing can significantly reduce the risk of a successful cyber attack, ensure compliance with regulations, and provide peace of mind. While there are no recommendations on how frequently you need to set pen testing services, one should remember that the digital age has already transformed how people develop systems, with bad actors and threats also adapting at the same rate.
Accepting that at any time, there may be a security issue that will stick its neck out, assessing one's vulnerability through a trusted pen testing service provider will ensure that no stones are left unturned.
Companies prioritizing cybersecurity through regular pen testing can gain a competitive advantage and build customer trust. There would be no more looking over their shoulders or worrying about what will happen next.

ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




