UPDATE: TechTimes has been contacted by a third-party spokesperson from Goldin Solutions clarifying "SolarWinds has determined that the credentials using that password were for a third-party vendor application and not for access to the SolarWinds IT systems. Furthermore, the third-party application did not connect with the SolarWinds IT systems. As such, SolarWinds has determined that the credentials using this password had nothing to do with the SUNBURST attack or other breach of the company's IT systems."
----
ORIGINAL STORY:
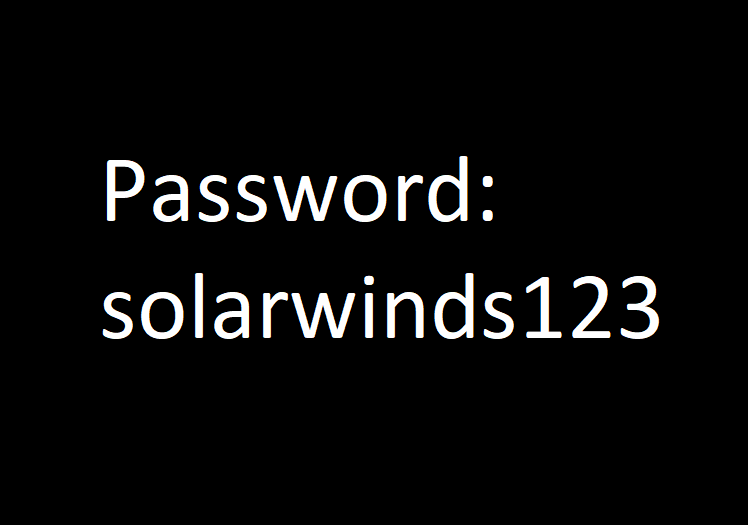
Several current and former top executives over at SolarWinds are now blaming a certain company intern for what was called a "critical lapse" in the company's password security that actually went sort of undiagnosed for a number of years. The supposedly leaked password was "solarwinds123" and was discovered back in 2019 on the internet by a particular independent security researcher that had warned the company regarding SolarWinds file servers being exposed.
How did SolarWinds get hacked?
Several U.S. lawmakers were ripped into the whole SolarWinds password issue in a recent joint hearing by the official House Oversight and Homeland Securities committees. The comments made by representative Katie Porter noted that she had stronger passwords than the basic "solarwinds123" to stop her kids from watching excessive YouTube on the laptop. She then noted that the company was supposed to be leading in the prevention of Russians from reading the Defense Department emails!
According to the story by CNN, Brad Smith, Microsoft President, who had also testified at the hearing, noted that there is actually no evidence that the United States pentagon was affected by the supposed Russian spying campaign. Microsoft is also one of the many companies that have led the forensic investigation into the whole hacking campaign.
What did the SolarWinds hack do?
Smith then told Porter that there is no indication to his knowledge that the official DoD was breached. The SolarWinds representatives told the lawmakers that as soon as the whole password issue was reported, it was then corrected in just a number of days. An article by Business Insider, however, still notes that a number of critical data were exposed.
However, it is still unclear as to what extent the leaked password enabled Russian hackers to access in order to spy on a number of federal agencies and businesses in what was known as one of the biggest security breaches ever in the history of the United States. Hackers had reportedly hidden a malicious code within the software updates and pushed it to about 18,000 customers as well as federal agencies.
What is SolarWinds attack?
Former SolarWinds CEO Kevin Thompson noted that the whole situation was a mistake that an intern had made. He even noted that the intern "violated" the company's password policies and had proceeded to post the password on their private Github account. He then noted that the company proceeded to take everything down as soon as the issue was identified.
There were no explanations as to why the company's technology would allow for this type of password. The current SolarWinds CEO, Sudhakar Ramakrishna, later revealed that the password had actually been used since early 2017.
Vinoth Kumar, the researcher responsible for discovering the leaked password, noted to CNN that it had been accessible ever since June 2018. SolarWinds and Kumar's emails show that this password allowed Kumar to secretly log in and successfully upload files on the company's critical server.
Related Article : SolarWinds Hack Update: Software Company Confirms No Products Were Affected; Here's Why It Was Breached
This article is owned by Tech Times
Written by Urian Buenconsejo
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




