Researchers of security firm ESET recently uncovered a malware backdoor called Crutch, which was implanted onto a European foreign ministry's systems. The malware was earlier linked to Turla hacking group, the same group that targeted Britney Spears' Instagram account in 2017.
Turla is described by ESET as cyberespionage group that targeted many governments and diplomatic entities worldwide. It has been active for more than 10 years and operates huge malware arsenal.

Computer Security Russian-linked Turla Hackers Target EU Foreign Ministry
Researchers linked the Crutch malware to the Russian hacking group Turla because of its similarities with previous campaigns launched by the group. The malware is actively used since 2015 and the recent attack is being done at similar timezone as that in Moscow.
According to an ESET report, the malware provides a secret backdoor designed to steal sensitive files and other documents through Dropbox accounts from compromised Windows systems controlled by hackers.
While ESET has not yet revealed any specific details about the target, the research firm noted that it was a ministry of foreign affairs of an EU member country, which suits the targeting of other Turla campaigns. The British National Cyber Security Centre (NCSC) also believed the recent attack is led by Turla, which is also known as Venomous Bear or Waterbug, under the orders of the Russian government.
Cyber Spying: How Crutch malware works?
ESET explained that the Crutch malware is not a first-stage payload. In fact, it is only installed once the cyber attackers already accessed the target network. Other similar campaigns successfully achieved such using specially-crafted attacks like spear-phishing.
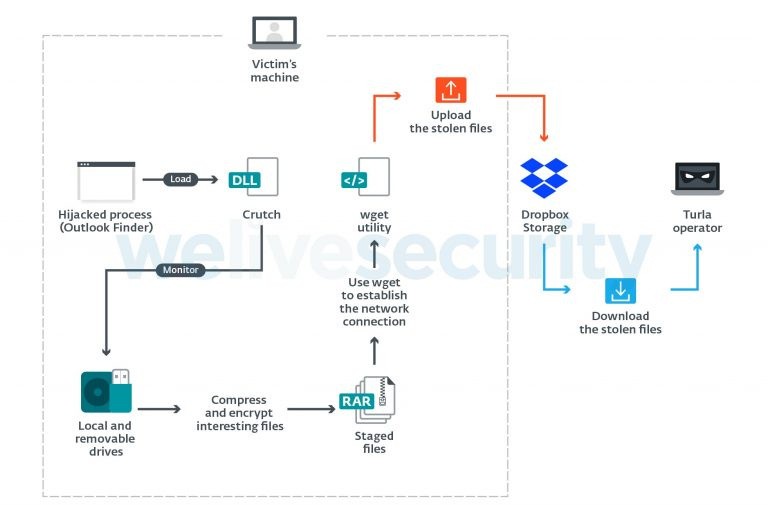
After deploying Crutch on the targeted system as a backdoor, hackers communicate using a hardcoded Dropbox account and utilize it to retrieve files. The act remains undetected since Dropbox could blend into normal internet traffic.
ESET malware researcher Matthieu Faou said the primary malicious activity held by the malware is the exfiltration of sensitive files and other documents. Faou also noted that with the "sophistication of the attacks and technical details of the discovery," the belief that the Turla hacking group has extensive resources and diverse arsenal, which it uses in their operations.
Meanwhile, the backdoor analysis shows that it has been constantly updated to maintain its effectiveness and remain hidden. Fortunately, organizations can still keep their systems secured using relatively simple measures to avoid becoming victims to cyber attacks despite the persistence of hackers with their sophisticated operations.
"We noticed that attackers were able to move laterally and compromise additional machines by reusing admin passwords," Fauo said.
Thus, by reducing lateral movement possibilities would greatly limit the hackers' access and make their lives quite harder. Fauo added that users should not be allowed to be able to run as admin, using complex and unique passwords, and having two-factor authentication on admin accounts.
Russian Turla group used Britney Spears's Instagram Account
In 2017, Tech Times reported that the Russian Turla hacking group has also deployed a sophisticated backdoor Trojan malware on popular social media site Instagram, particularly pop icon Britney Spears' account. Spears' account was allegedly used as Turla's secret command center, although it did not mean to hijack account users.
The security firm referred such type of hack as "watering hole" attack, which has been active since 2014 and employs different techniques to direct users to hackers' command and control infrastructure.
In Spears' Instagram posts, hackers wrote comments, which are linked to a central server that conveyed instructions and transferred stolen data between compromised computers.
Spears's Instagram was used as a relay system to shield hackers and kept their C&C server concealed.
"The websites' visitors will be redirected to a malicious server because of a snippet - inserted by the attacker - appended to the original page," ESET explained.
Related article: Oops, They Did It Again: Russian Hackers Tapped Britney Spears's Instagram Account To Post Coded Messages
This is owned by Tech Times
Written by CJ Robles

![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)


