Security firm Check Point discovers a new malware called WAPDropper that spreads through malicious apps and targets users in Southeast Asia.
The malware victims are charged for expensive premium mobile services once they downloaded the apps. The attack is similar to the ones that became popular in the late 2000s.

How WAPDropper Malware works?
Check Point security researchers said the new Android malware are acquired using malicious apps from third-party app stores. Once the malware gets through, it signs up users for premium phone numbers, which charge huge fees for different services. Meanwhile, a CAPTCHA step is sometimes required to finalize the subscription.
This results to large phone bills every month until they contact their mobile provider to file a report about the issue or unsubscribe from the premium number.
This kind of attack became popular in the late 2000s, but vanished later as smartphones came out. However, it managed to return in the early 2010s after cyberattackers found that there are numerous telephone companies and modern phones that still used the older WAP standard.
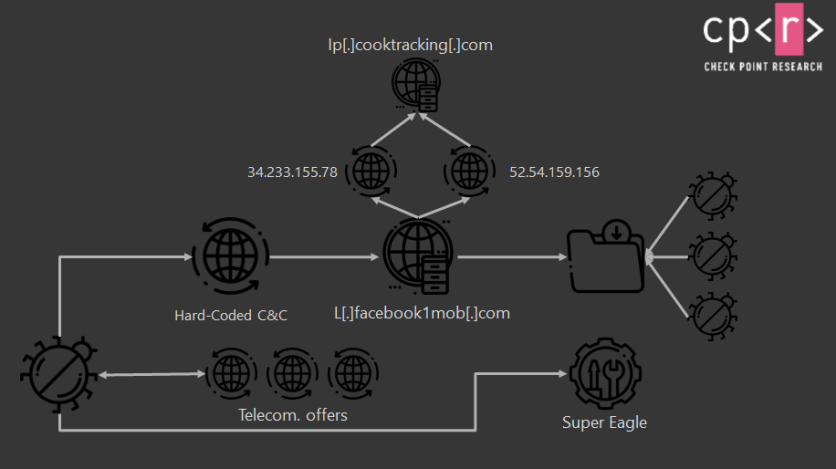
According to Check Point, the WAPDropper operated using two modules: the dropper and the component that implemented the actual WAP fraud.
The first module was packed inside the malicious apps, which reduces the fingerprint and size of malicious code. Once victims downloaded these apps and installed them on the device, the module would download the second component, which would begin swindling the users.
Read also: Cybercriminals Now Target Google Workspace Tools: 5 Phishing Campaigns Use Form, Docs, and Sites
WAPDropper Malware attackers from Southeast Asia
Check Point researchers claim that upon checking the premium phone numbers that were used in this malware scheme, the cybercriminals are likely to be from Malaysia or Thailand. It is also possible that they are working with people from these countries.
Researchers said the attack is a numbers game, in which more revenue is generated with more calls made with the premium-rate services. "Everybody wins, except the unfortunate victims of the scam," CheckPoint wrote in a blog.
However, Check Point Mobile Research Manager Aviran Hazum warned about the future risks that WAPDropper could bring.
"Right now, this malware drops a premium dialer, but in the future this payload can change to drop whatever the attacker wants," Hazum told ZDNet
Hazum noted that this multi-function 'dropper' could be installed stealthily onto the victim's mobile phone and later downloads other malware. This mode of mobile infection was seen between January and July 2020 when 'dropper' trojans comprised about half of all mobile malware attacks that infected hundreds of millions across the world. He added that the trend is expected to continue until 2021.
How to prevent WAPDropper malware
To avoid getting infected by WAPDropper Malware, Check Point researchers urge users to only download Android apps from the Google Play Store.
Meanwhile, security researchers also added that the WAPDropper malware was found inside applications such as "dolok," "af," "Email" as well as the "Awesome Polar Fishing" game app, which were downloaded and installed from outside the Play Store. Although it is possible the accounts have been compromised already, Check Point advises users to immediately remove these apps from their devices.
Related article: TCL Smart TVs Have 'Backdoor' Security Flaw, Experts Find - Here's How to Protect Your TV
This is owned by Tech Times
Written by CJ Robles

![Apple Watch Series 10 [GPS 42mm]](https://d.techtimes.com/en/full/453899/apple-watch-series-10-gps-42mm.jpg?w=184&h=103&f=9fb3c2ea2db928c663d1d2eadbcb3e52)


