Tesla is reportedly creating a new patch as a hacker was able to get through a Tesla Model X using key cloning relay attack within 90 seconds.
While Tesla added security features with an improved key fob cryptography as well as an optional PIN to Drive feature in response to sophisticated relay attacks to steal Tesla vehicles in Europe and North America, a Belgian university KU Leuven security researcher claims to have been able to develop new hacks to go around the enhanced cryptography in the key fob.

New Key Cloning Relay Attack: How to Get Entry to a Tesla Model X in 90 Seconds
Lennert Wouters explained to Wired how he was able to perform the hack and get away with a Tesla Model X in just 90 seconds. Wouters took advantage in a series of security issues he found within the Tesla's keyless entry system. After combining these issues, it allowed to fully unlock, start, and get away with the vehicle.
The information provided to Wired is only the first part as Wouters revealed the whole process is actually two parts. It should be noted that the Model X's key fobs lack "code signing" during their firmware updates as Tesla sends firmware updates over-the-air. These updates are received by the key fobs through Bluetooth by connecting wirelessly to the Model X computer.
Despite having an unforgeable cryptographic signature from Tesla, Wouters discovers that he could use the Bluetooth on his own computer to connect to the Model X's keyfob. Then, he would rewrite the firmware and use it to secure the fob's enclave chip, which generates a code to unlock the vehicle, after which, he sends back the code to his computer via Bluetooth.
Drive away a Model X in a minute
It took Wouters only about 90 seconds to get entry to the vehicle, which is only the first part. The second part of the hack begins once Wouters is already inside the vehicle.

As the first part allowed Wouters to enter the locked vehicle, unlocking and driving is the harder part. Wouters discovered that he could actually connect his computer into a certain port inside the Model X, which can be easily done within seconds by hand. Just pull off the small storage container on the dash as the port is accessible only through a small panel located under the display. This port allows the computer to send commands to the car's CAN bus or the internal component network, including the BCM.
After which, Wouters could then initiate the Model X's BCM to pair using his own key fob, which essentially tells the car that the cloned key is authentic. Although Tesla provide a unique cryptographic certificate on each Model X key fobm which should have prohibited the pairing with the fake key, Wouters discovered that the BCM does not check the certificate.
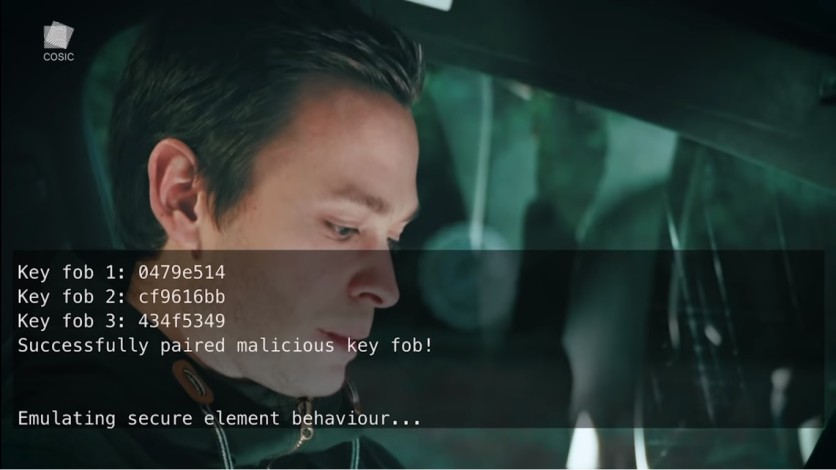
While it is not yet clear if the second part of the trick can be prevented using Tesla's PIN-to-Drive feature which asks driver to enter a PIN to activate the vehicle, the fact is Wouters was able to use his own key and drive the vehicle away after just a minute.
After advising Tesla about his hacking tricks in August, Wouters said the electric carmaker told him that they will begin pushing another software update anytime this week to patch his hack.
Watch the hack demonstration on this YouTube video:
Related article: Tesla Issues Warning to Owners Hacking Their Vehicle to Avoid Paying $2K Acceleration Boost
This is owned by Tech Times
Written by CJ Robles
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




