Sonatype security researchers found malicious code in an npm package, which is designed to steal sensitive files from Google Chrome, Brave, Opera, Yandex browsers and Discord application.
Sonatype is a security company that offers developer security operations (DevSecOps) services, so it also monitors public package repositories. The company said discord.dll has been downloaded for more than 100 times since it was published over five months ago.

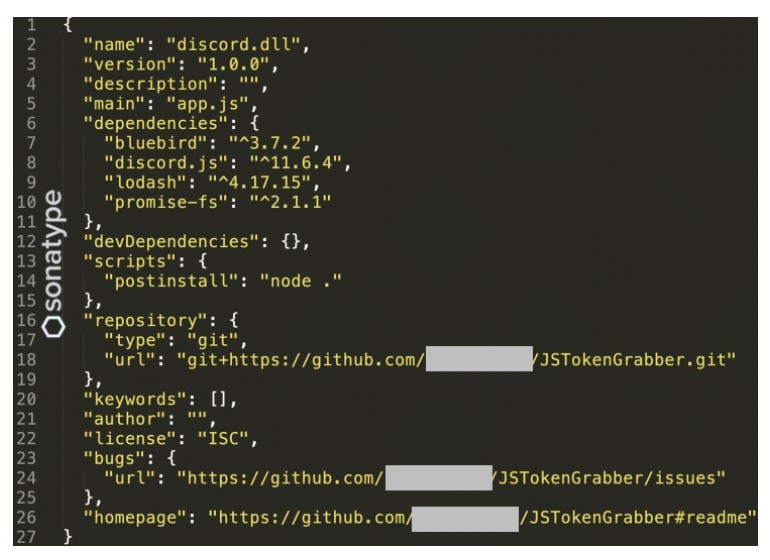
According to ZDNet, the malicious JavaScript library called discord.dll is still available in the web portal npm, Inc. Founded in 2014, the company is a package and command-line utility manager for JavaScript programmers. Developers use the site to load and update their libraries within their JavaScript projects, including desktop apps, server applications, or websites.
In March, GitHub acquired npm, which is a vital to the JavaScript community, providing support in one of the world's largest ecosystems of developers.
Discord malware
Sonatype researchers wrote in a blog article that after installing discord.dll, it will run a malicious code to search for certain apps within the user's computer and retrieve internal LevelDB databases.
These files are used by the Discord instant messaging app, which is currently popular among online gamers, as well as browsers such as Google Chrome, Brave, Opera, and Yandex. These apps use LevelDB databases files to store information like access tokens and browsing histories. Once accessed, Discord.dll would read these files and attempt to post them in a Discord channel.

Although Sonatype has already advised the npm security team about the discord.dll, the package is still shown on the npm portal while researchers said it is likely to be removed soon.
Meanwhile, researchers discovered the author of discord.dll had uploaded 10 more packages on the npm site. Among these packages, three libraries included malicious behavior, which would download and activate three mysterious EXE data.
However, researchers cannot fully confirm the nature of the three libraries, which include ac-addon, wsbd.js, and discord.app since they could not retrieve these EXE files. This is not a standard behavior for npm's JavaScript packages.
Malware specs and timeline
Here are some interesting details of the about these packages, including number of downloads and timeline:
- discord.dll - 100 download, published five months ago
- discord.app - 88 downloads, published 5 months ago.
- ac-addon - 46 downloads, published 14 days ago.
- wsbd.js - 38 downloads, published 21 hours ago.
Enhanced version of another malicious NPM package
After reviewing the malware, Sonatype discovered the malicious code was an enhanced version of fallguys, which is the malicious library it found in September. The fallguys package was also collecting similar information in a more simplified way.
The fallguys package has been downloaded over 300 times, but it was only available for only two weeks on the npm portal. Its success is related to the fact that fallguys also included a README file, which advertised the library as interface for "Fall Guys: Ultimate Knockout" game API. On the contrary, the discord.dll package shows an empty README, which suggests that it was never "officially" launched or abandoned by the creator.
Related article: New Microsoft Office 365 Phishing Attack Tricks Anti-phishing Software Using Color Inversion and CSS code
This is owned by Tech Times
Written by CJ Robles
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




