As more companies move to virtual offices and transactions, more incidents of data leaks and hacking attacks are reported. With this, organizations and consumers alike are concerned about their security online. There are many questions about this that linger in the minds of every online enterpreneur.
To shed light on some of these queries, we will share with you some insights from Mana Security CEO and founder Tim Ismilyaev. TechTimes was given the oppurtunity to interview the famed cyber expert about this topic.

TechTimes: We'd love to hear about how the company started. What moved you to establish this company?
CEO Tim Ismilyaev: We were building security for Cindicator Capital, a hedge fund for crypto assets. Our defense system consisted of fundamental security measures and a detection/response team for advanced threats. We noticed that vulnerability management parts frequently required our attention: every day, new vulnerabilities appeared for apps we used for daily work-Microsoft Office, browsers, developers' tools, and many others.
These vulnerabilities could stay unpatched for months if our cyber team manually didn't notify colleagues about them. It usually required 3-4 pings within a few weeks before our colleagues solved the problem. For a team of our size (70+ people), it occupied 20% of two security engineers' time. That is a lot because we always had a ton of work in other parts of security processes.
It became apparent that the current vulnerability management approach was invented 20-30 years ago when companies had much fewer apps to maintain. So cyber teams could easily manage to verify that all systems run the latest software.
We started to investigate how other cyber teams tackle this issue. We figured out that most teams use one of the following approaches:
- regular manual reminders;
- has a dedicated VM team that find the most critical updates and then asks IT engineers to fix the shortlist;
- enforce a whitelist of apps for all company computers/servers and has a maintenance hour to update them in the morning.
None of these solutions worked well for most SMBs and us. We came up with an idea to delegate the update process to team members and incentivize them using game mechanics used in MMO games. After successful trials of this approach in several companies, we decided to launch a new company to help other teams to solve this problem in their organizations.
TechTimes: Can you please tell us about what Mana Security does? How does it work?
CEO Tim Ismilyaev: I regularly play many computer and mobile games, including Dota 2, Hero Wars (mobile MMO RPG), and learn Spanish in Duolingo. All these apps have many mechanics to keep gamers return to their apps, and we use some of them in Mana.
When our users install updates for apps on their workstation, we reward them with points. Mana announces who was best in security this week and who failed to update at the end of each week. When you fail to update on time, you put your company at risk, and this motivates people to be more active next week.
The other mechanic is to make daily updates more interesting: we split all employees into pairs and notify each side about their opponent. They both have a few hours to install updates. If one fails to complete tasks on time, she loses some points, and the other side gets additional rewards.
Most employees usually have 2-3 updates to install per week. So when they don't have vulns, we reward them with "daily chests" for staying secure. It becomes a routine for clients: many start their day by opening "daily chests" and getting a portion of dopamine by helping the company to stay secure.
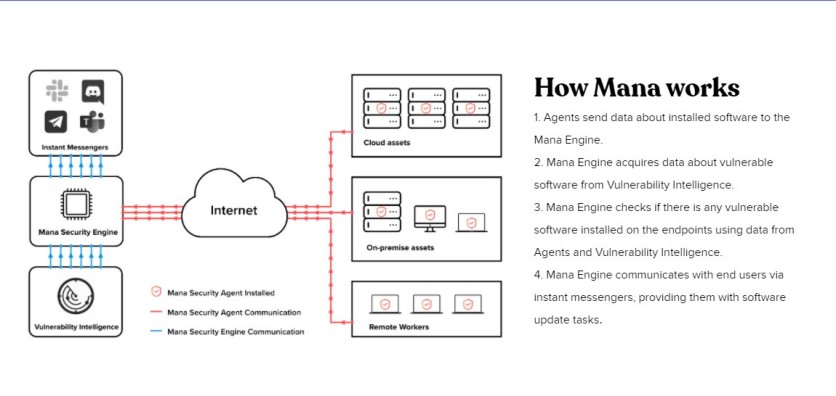
TechTimes: Some are saying that no matter how secured a server or platform is, hackers can still get into it. Is this true? What are your thoughts about different hacking incidents?
CEO Tim Ismilyaev: Statistics show that most data breaches could be stopped if companies followed simple rules: updated apps on time and had the right hardening policies. Both rules aren't that hard to implement and don't break end-users' experience. Criminals aren't interested in most businesses, so when they fail to break into a company in 1-2 attempts, they switch to other targets with a less robust defense.
The rest data breaches usually comprise businesses with high stakes: financial institutions, popular e-commerce platforms. Adversaries can spend much more time on them because they have a higher upside: steal millions from bank accounts or get a ransom for unpausing the company's operation.
The goal of defense for these companies is to make an attack much longer in time, leaving multiple traces during the attack. Even when they use a 0-day vulnerability, they still have to execute malicious code and put a backdoor. There're plenty of techniques to detect these actions, and then security teams would be able to react to it. For example, Coinbase detected malicious actors who used 0-day for Firefox, quickly isolated affected workstations, and stopped the targeted attack.
TechTimes: In what way can you help with an organization's data protection and cybersecurity? What needs to be done by companies and organizations to avoid data breach?
CEO Tim Ismilyaev: Any attack starts from two major attack vectors:
- exploiting missing patches during reconnaissance;
- sending phishing emails.
According to recent researches (Ponemon Institute - 60%, Automox - 58%), the first vector is the most popular. Mana Security helps a lot with it, because when a business fixes vulnerabilities on time, there're no easy paths to intrude the company.
We met potential customers during our sales and noticed that their cyber teams focus on the wrong parts of security. Instead of building fundamental security first, they start to developing detection&response processes and systems. The costs to build D&R ranges from $200k (Red Canary estimation) to $1.2M...2.4M (LINKBYNET estimations) per annum.
For SMBs I recommend implementing fundamental security first. It's fast to build, and one security engineer can easily maintain it. The fundamental security consists of several pieces:
- Mandatory 2FA.
- Password managers.
- Installing app/OS updates within 1-2 weeks.
- Hardening. Specify attack vectors from MITRE ATT&CK for relevant OSes and harden them.
- Unified endpoint management. It is used to distribute hardening policies across all workstations.
- Binary whitelisting.
- Enforce the same OS: one for workstations and one for servers. It's much easier to protect a limited amount of operating systems, especially when you have one or two security engineers.
- Do backups of all workstations and store them offline. In case of a ransomware attack, you'll be able to resume normal business operations.
TechTimes: Is Mana Security designed for teams or organizations or does it also work for individuals (say, influencers)?
CEO Tim Ismilyaev: We now only focus on products for businesses because they realize the problem much better.

TechTimes: What's your advice to online users to ensure privacy and data protection when using social media, emails, etc?
CEO Tim Ismilyaev: The bare minimum for personal computers and smartphones:
- Install updates within 1-2 weeks.
- Use two accounts on a computer: the non-administrative account for daily tasks and the account with admin permissions for the occasional cases. If you see an unexpected popup that requires admin permission, safely press "Cancel."
- Utilize 2FA, at least for essential accounts: email, social networks, banking, messengers, smartphones.
- Use Password manager - it helps to create strong unique passwords for each application/service and store them in secured encrypted storage.
- Use apps only from native app stores: Mac App Store, Windows Store, iOS App Store, Google Play. They have security verification tests, so it's hard for crooks to get there. As a last note: never use Torrent clients. They connect to thousands of suspicious computers while downloading files-there're many cases when attackers easily compromised computers utilizing a vulnerability in popular Torrent clients.
For more advanced users I strongly recommend hardening running new software on computers. This way, even if a criminal will try to execute some malicious program on your PC, he'll fail:
- Install binary whitelisting on personal computers: Google Santa for macOS and AppLocker for Windows. They prevent running unknown software if you don't allow them explicitly. It's a bit hard in the beginning, but it will pay off in the future many times.
- Consider uninstall or blacklist developer tools (bash, python, etc.) if you don't require them.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




