
Last week, tech experts warned citizens all over the world to never open and download emails disguised as "Coronavirus emails" found on their accounts.
According to them, these files hold suspicious malware that can steal the personal information from the user that will download the said email.
[WARNING] Don't open this email amid coronavirus outbreak
On Jan. 30, experts from IBM X-Force Threat Intelligence reported on what they found as "spam emails" that may affect anyone that will download the said file. As mentioned, hackers have been sending emails that explain the threat and danger involving the Coronavirus outbreak to victims on Japan, causing them to voluntarily downloading and opening the said file.
Most of the emails were scaring Japanese citizens that another Coronavirus victim was found positive from their region which then, urges them to download and open an attached Microsoft Word that holds the said "infection prevention measures" that must be done immediately.
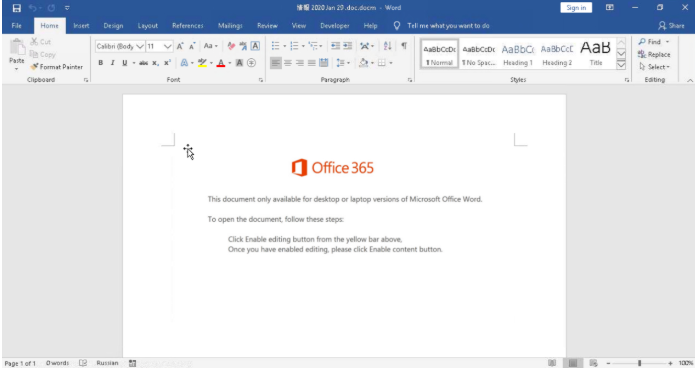
Once you downloaded the said Coronavirus prevention email, the file will then pop an MS word that will show an unsupported word format and a message from Office 365 that instructs the viewer to enable the content just in case it was opened in protected view.
The report said that after opening it, hackers would instantly upload malware on the computer or smartphone and have access to the user's accounts.
Emotet malware spreads fake coronavirus information
Investigations found out that famous malware called 'Emotet' was behind all these fake Coronavirus emails that have been circulating in Japan.
"Emotet is a kind of malware that is originally designed as a banking Trojan aimed at stealing financial data," according to report.
It was first reported in 2014 and had the same method of forcing users to open a specific file for them to steal financial information or any personal information that will then give them the ability to hijacked various accounts from the victim.
"Previously, Japanese Emotet emails have been focused on corporate style payment notifications and invoices, following a similar strategy as emails targeting European victims. This new approach to delivering Emotet may be significantly more successful, due to the wide impact of the coronavirus and the fear of infection surrounding it," said the report.
How to prevent being a victim of Emotet malware?
Due to the spread of these hacking schemes, the government of Singapore already reminded its citizens never to download and only trust credible sources regarding information about the Coronavirus disease.
"Users are reminded not to click on links or open attachments found in suspicious-looking emails or messages," said on their website.
IBM also gave their recommendations for all gadget users around the world.
- Do not click or open links in emails directly, instead type in the main URL in your browser or search the brand/company via your preferred search engine.
- Ensure anti-virus software and associated files are up to date.
- Search for existing signs of the indicated IOCs in your environment.
- Block all URL and IP based IOCs at the firewall, IDS, web gateways, routers, or other perimeter-based devices, a course of action, resources, or applications to remediate this threat.
- Keep applications and operating systems running at the current released patch level.
As of Sunday, Feb. 2, over 350 Chinese victims were already reported dead after being infected with the outbreak.
ALSO READ: How do Facebook, Twitter, and Google Plan to Stop Spread of Coronavirus Misinformation and Conspiracy Theories?
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




